70-14
Cisco ASA 5500 Series Configuration Guide using ASDM
Chapter 70 Configuring Dynamic Access Policies
DAP and Authentication, Authorization, and Accounting Services
• Test Result—Displays the result of the test.
• Test—Click to test the retrieval of the policies you have set.
• Close—Click to close the pane.
DAP and Authentication, Authorization, and Accounting
Services
DAP complements AAA services. It provides a limited set of authorization attributes that can override
those AAA provides. The ASA selects DAP records based on the AAA authorization information for the
user and posture assessment information for the session. The ASA can select multiple DAP records
depending on this information, which it then aggregates to create DAP authorization attributes.
You can specify AAA attributes from the Cisco AAA attribute hierarchy, or from the full set of response
attributes that the ASA receives from a RADIUS or LDAP server. For more information about DAP and
AAA, see the section, Configuring AAA Attributes in a DAP.
Configuring AAA Attributes in a DAP
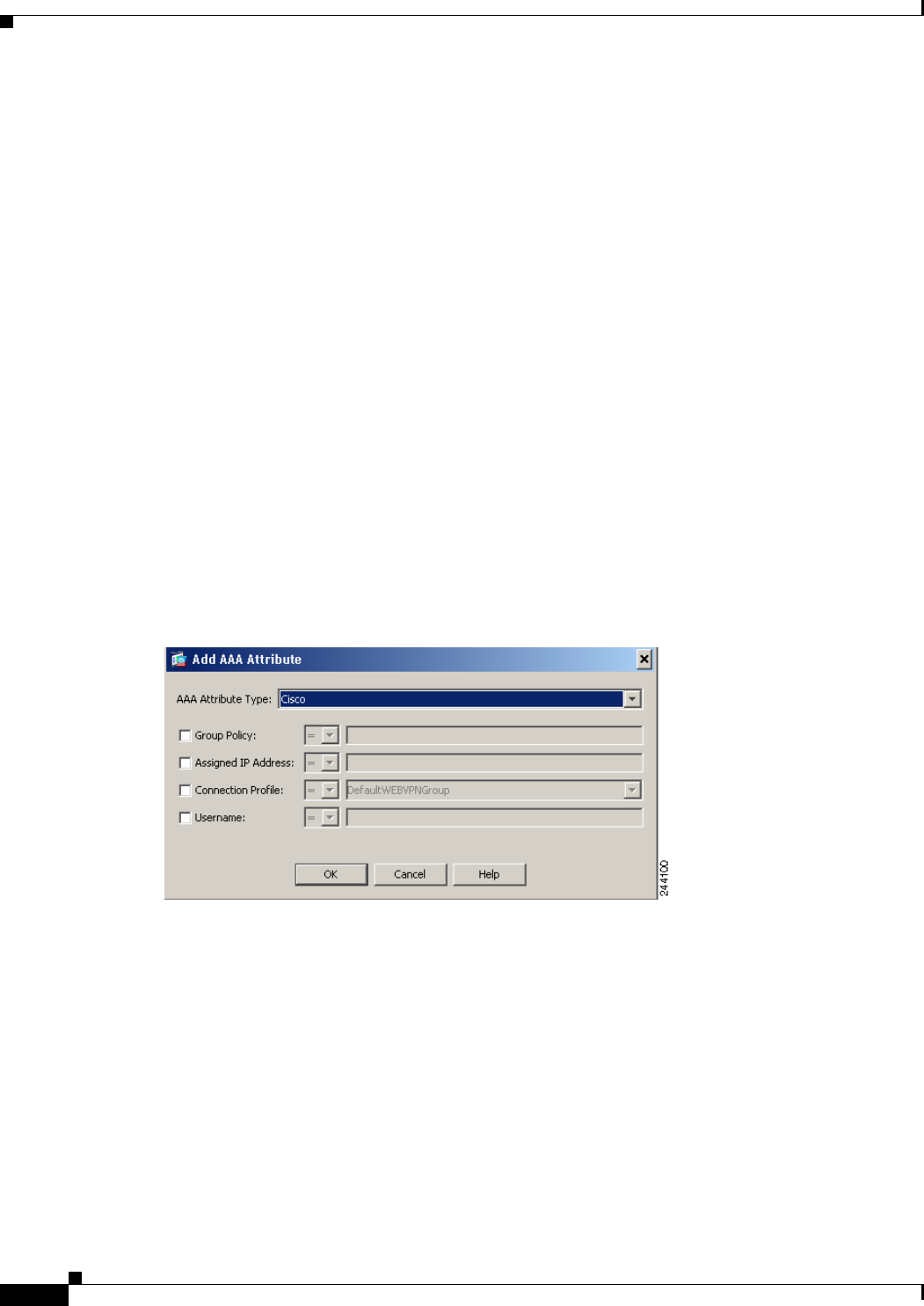
Figure 70-4 shows the Add AAA Attribute dialog box.
Figure 70-4 Add AAA Attribute Dialog Box
To configure AAA attributes as selection criteria for DAP records, in the Add/Edit AAA Attributes
dialog box, set the Cisco, LDAP, or RADIUS attributes that you want to use. You can set these attributes
either to = or != the value you enter. There is no limit for the number of AAA attributes for each DAP
record. For detailed information about AAA attributes, see AAA Attribute Definitions.
Fields
AAA Attributes Type—Use the drop-down list to select Cisco, LDAP or RADIUS attributes:
• Cisco—Refers to user authorization attributes that are stored in the AAA hierarchical model. You
can specify a small subset of these attributes for the AAA selection attributes in the DAP
record.These include:
–
Group Policy —The group policy name associated with the VPN user session. Can be set locally
on the security appliance or sent from a RADIUS/LDAP server as the IETF-Class (25) attribute.
Maximum 64 characters.


















