Configuration
222 AlterPath KVM/net Installation, Administration, and User’s Guide
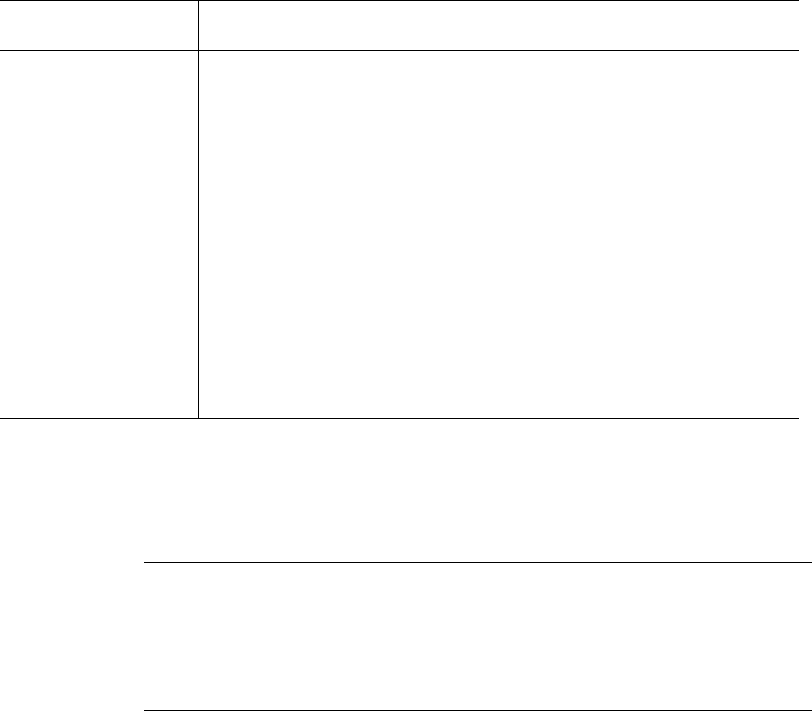
The following table show the enabled protocols and services under each
Security Profile.
Custom Security Profile
The Custom Security Profile opens up a dialog box to allow custom
configuration of individual protocols and services.
Caution! By default a number of protocols and services are enabled in the Custom
Security Profile, however, the protocols and services are user configurable for
site specific requirements. Take the required precautions to understand the
potential impacts of each individual service configured under Custom
Security Profile.
The following table show the available protocols and services under the
Custom Security Profile.
Table 4-6: Enabled Protocols and Services under each Security Profile
Security Profile SSH Access Web Access Protocols
Secured
• SSHv2 • HTTPS
Moderate
(Default)
•SSHv1
•SSHv2
• SSH root access
• HTTP
• HTTPS
• HTTP redirection to
HTTPS
•ICMP
Open
•SSHv1
•SSHv2
• SSH root access
Direct Access to
KVM Ports
• HTTP
• HTTPS
•Telnet
•SNMP
•RCP
•ICMP


















