Chapter 8 L2TP VPN Example
ZyWALL USG 300 User’s Guide
210
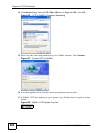
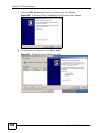
11 Select Use this string to protect the key exchange (preshared key), type
password in the text box, and click Next.
Figure 204 IP Security Policy Properties: Authentication Method
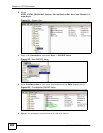
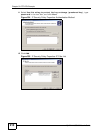
12 Click Add.
Figure 205 IP Security Policy Properties: IP Filter List