ZyWALL USG 300 User’s Guide
441
CHAPTER 23
Authentication Policy
23.1 Overview
Use authentication policies to control who can access the network. You can
authenticate users (require them to log in) and even perform Endpoint Security
(EPS) checking to make sure users’ computers comply with defined corporate
policies before they can access the network. After a users passes authentication
the user’s computer must meet the endpoint security object’s Operating System
(OS) option and security requirements to gain access. See Chapter 49 on page
799 for how to configure endpoint security objects to use with authentication
policies.
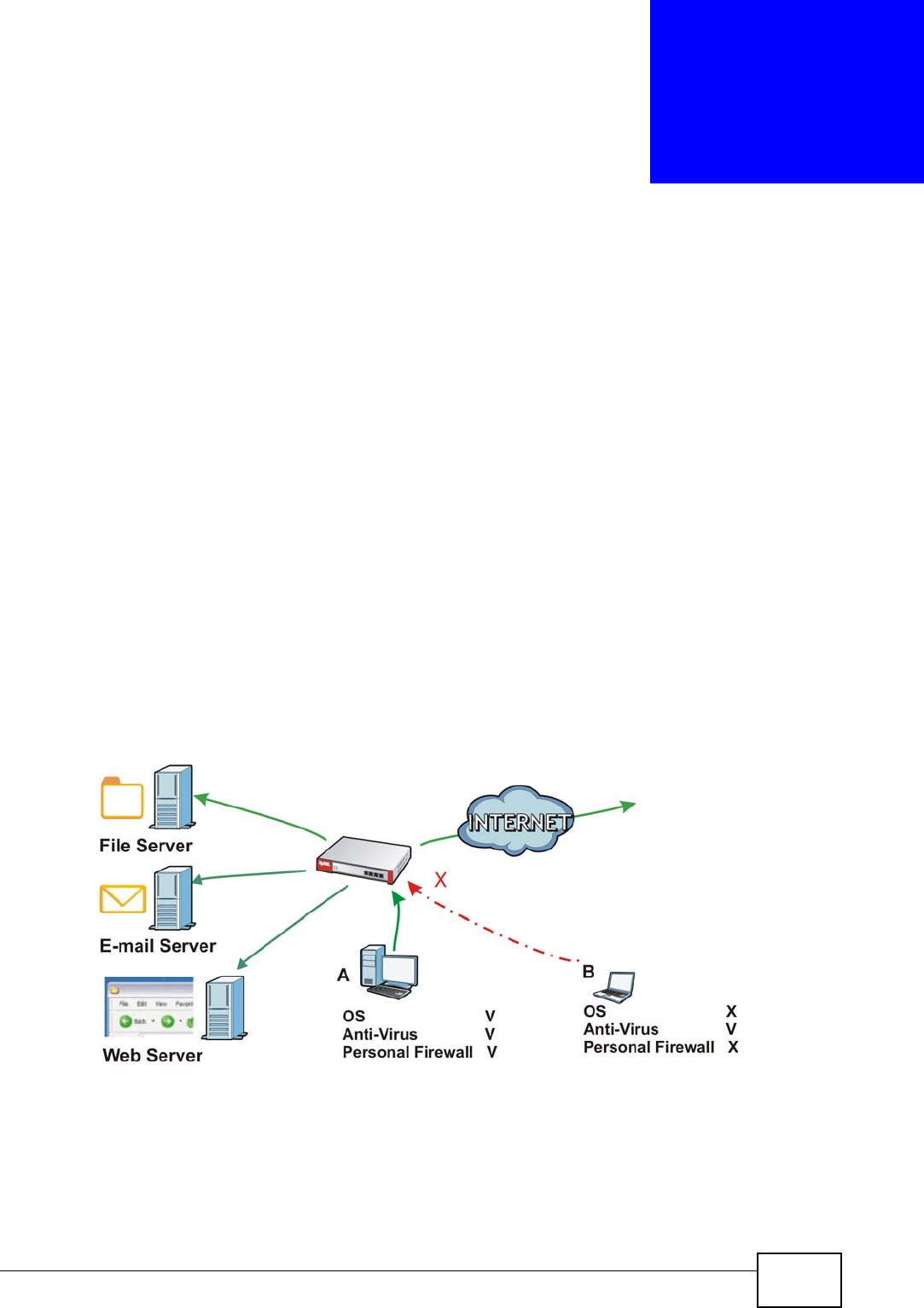
In the following figure the ZyWALL’s authentication policy requires endpoint
security checking on local user A. A passes authentication and the endpoint
security check and is given access. Local user B passes authentication but fails the
endpoint security check and is denied access.
Figure 333 Authentication Policy Using Endpoint Security
23.1.1 What You Can Do in this Chapter
Use the Configuration > Auth. Policy screens (Section 23.2 on page 442) to
create and manage authentication policies.