292 CHAPTER 17: NETWORK PROTOCOL OPERATION
Configuration Example I. Network requirements
As shown in Figure 71, the Ethernet1/0/1 port of Switch A (an S5500 series switch) is
connected to Switch B (acting as a DHCP relay). A network segment containing some
DHCP clients is connect to the Ethernet1/0/2 port of Switch A.
■ The DHCP snooping function is enabled on Switch A.
■ The GigabitEthernet1/0/1 port of Switch A is a trusted port.
Configuration procedure
1 Enter system view.
<S5500> system-view
2 Enable the DHCP snooping function.
[S5500] dhcp-snooping
3 Enter Ethernet1/0/1 port view.
[S5500] interface Ethernet1/0/1
4 Set the port to a trusted port.
[S5500-Ethernet1/0/1] dhcp-snooping trust
Introduction to DHCP
Accounting
DHCP accounting allows a DHCP server to notify the RADIUS server of the start/end of
accounting when it assigns/releases a lease. The cooperation of DHCP server and
RADIUS server implements the network accounting function, and at the same time
secures the network to a certain degree.
Structure of the DHCP
Accounting Packets
The interaction between the DHCP server and the RADIUS server are based on two
types of packets: Accounting START request and Accounting STOP request. The two
types of packets have the similar structure, but are slightly different in the Attributes
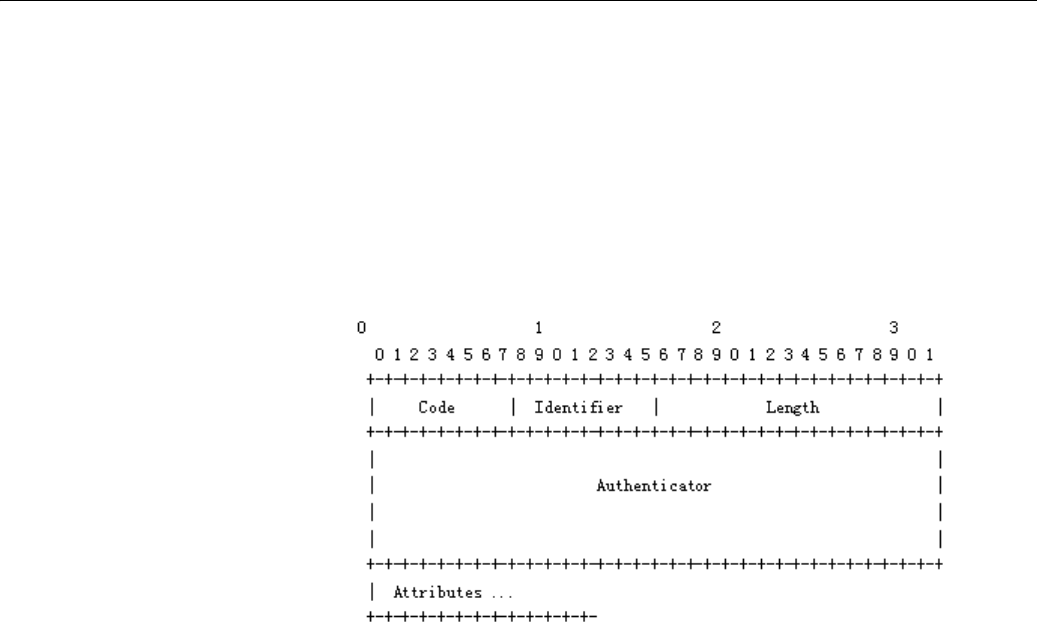
field. Figure 72 illustrates the packet structure.
Figure 72 Structure of the DHCP accounting packets
■ Code: One byte, identifying the type of the RADIUS packet. A packet with an
invalid Code filed will be discarded. A value of 4 indicates this is a RADIUS START
request, while a value of 5 indicates this is a RADIUS STOP request.
■ Identifier: One byte, identifying the requests and the responses. The RADIUS server
checks this field for duplicate requests from the same IP address and UDP port of a
client.


















