506 CHAPTER 22: FILE SYSTEM MANAGEMENT
SSH Terminal Services Secure Shell (SSH) can provide information security and powerful authentication to
prevent such assaults as IP address spoofing, plain-text password interception when
users log on to the Switch remotely from an insecure network environment. A Switch
can connect to multiple SSH clients. SSH Client functions to enable SSH connections
between users and the Switch or UNIX host that support SSH Server. You can set up
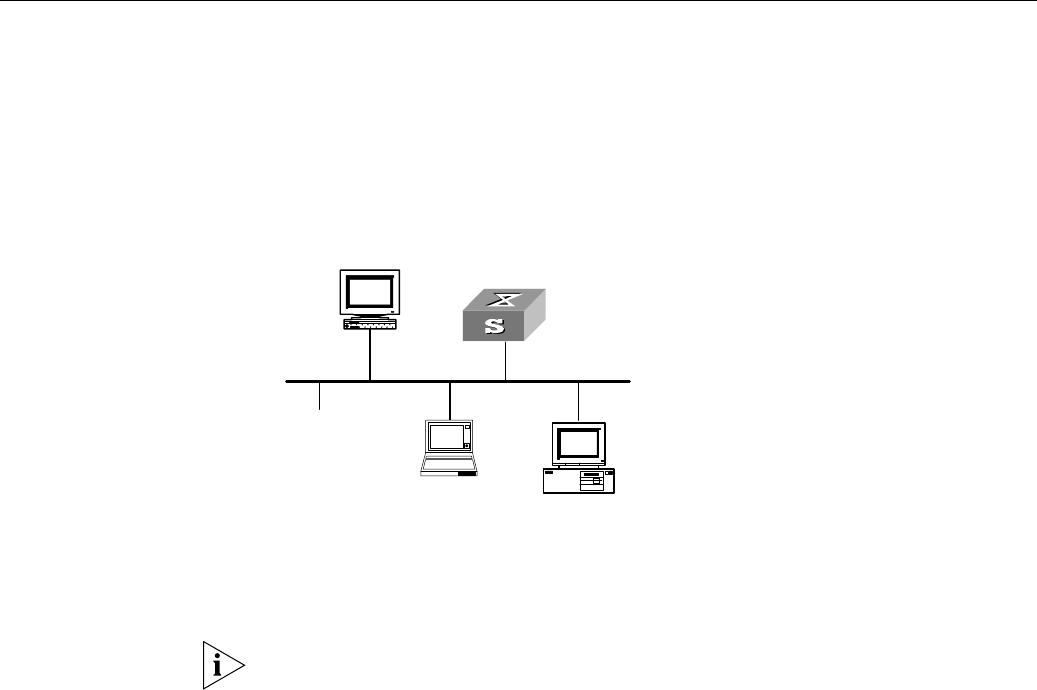
SSH channels for local connection. See Figure 133.
Currently the Switch that runs SSH server supports SSH version 1.5.
Figure 133 Setting up SSH channels in LAN
1: Switch running SSH server
2: PC running SSH client
3: Ethernet LAN
In Figure 133, the VLAN for the Ethernet port must have been configured with VLAN
interfaces and IP address.
The communication process between the server and client include these five stages:
version negotiation stage, key negotiation stage, authentication stage, session
request stage, interactive session stage.
■ Version negotiation stage: The client sends TCP connection requirement to the
server. When TCP connection is established, both ends begin to negotiate the SSH
version. If they can work together in harmony, they enter the key algorithm
negotiation stage. Otherwise the server clears the TCP connection.
■ Key negotiation stage: Both ends negotiate key algorithm and compute session
key. The server randomly generates its RSA key and sends the public key to the
client. The client figures out session key based on the public key from the server
and the random number generated locally. The client encrypts the random
number with the public key from the server and sends the result back to the server.
The server then decrypts the received data with the server private key to get the
client random number. It then uses the same algorithm to work out the session
key based on server public key and the returned random number. Then both ends
get the same key without data transfer over the network, while the key is used at
both ends for encryption and description.
■ Authentication stage: The server authenticates the user at the client after
obtaining a session key. The client sends its username to the server: If the
username has been created and configured as no authentication, authentication
stage is skipped for this user. Otherwise, the authentication process continues.
SSH supports two authentication types: password authentication and RSA
authentication. In the first type, the server compares the username and password
received with those configured locally. The user is allowed to log on to the Switch
if the usernames and passwords match exactly. RSA authentication works in this
2
3
1