HWTACACS Protocol Configuration Example 621
HWTACACS Protocol
Configuration
Example
For the hybrid configuration example of AAA/RADIUS protocol and 802.1x protocol,
refer to Configuration Example in 802.1x Configuration. It will not be detailed here.
Configuring the
FTP/Telnet User
Authentication at a
Remote TACACS Server
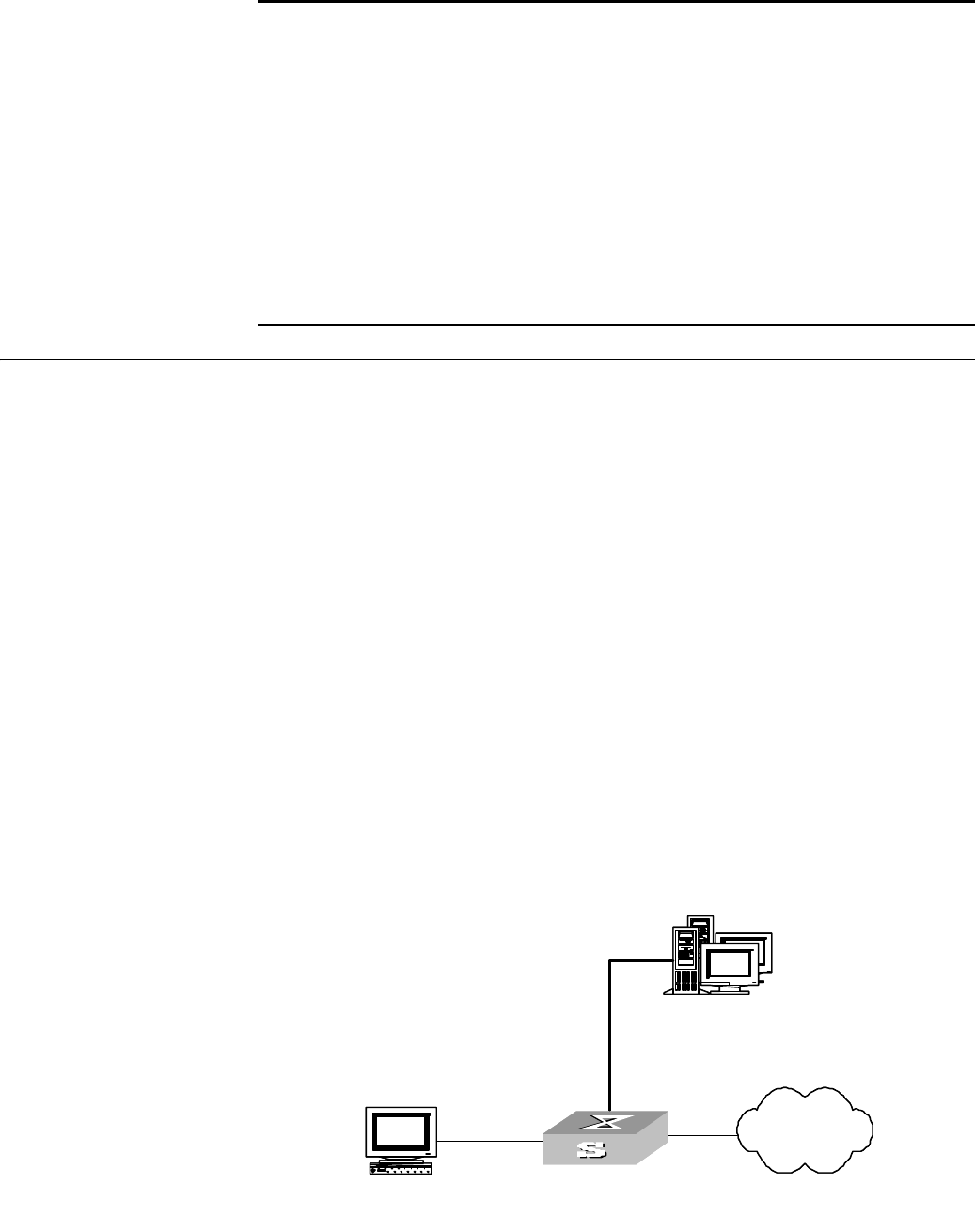
Networking requirements
Configure the switch to use a TACACS server to provide AAA services to login users
(see Figure 177).
Connect the switch to one TACACS server (providing the services of authentication
and authorization) with the IP address 10.110.91.164. On the switch, set the shared
key for AAA packet encryption to “expert”. Configure the switch to send usernames
to the TACACS server with isp-name removed.
On the TACACS server, set the shared key for encrypting the packets exchanged with
the switch to “expert”; add the usernames and passwords of users.
Networking diagram
See Figure 177.
Networking topology
Figure 177 Configuring the remote RADIUS authentication for Telnet users
Reset the statistics of HWTACACS server reset hwtacacs statistics { accounting |
authentication | authorization | all }
Enable RADIUS packet debugging debugging radius packet
Disable RADIUS packet debugging undo debugging radius packet
Enable debugging of local RADIUS
authentication server
debugging local-server { all | error | event |
packet }
Disable debugging of local RADIUS
authentication server
undo debugging local-server { all | error |
event | packet }
Enable HWTACACS debugging debugging hwtacacs { all | error | event |
message | receive-packet | send-packet }
Disable HWTACACS debugging undo debugging hwtacacs { all | error | event
| message | receive-packet | send-packet }
Table 684 Displaying and debugging AAA and RADIUS/HWTACACS protocol (continued)
Operation Command
Authentication Servers
( IP address:10.110.91.164 )
Internet
Switch
telnet user
Internet


















