6-6 Sun StorEdge 5310 NAS Troubleshooting Guide • December 2004
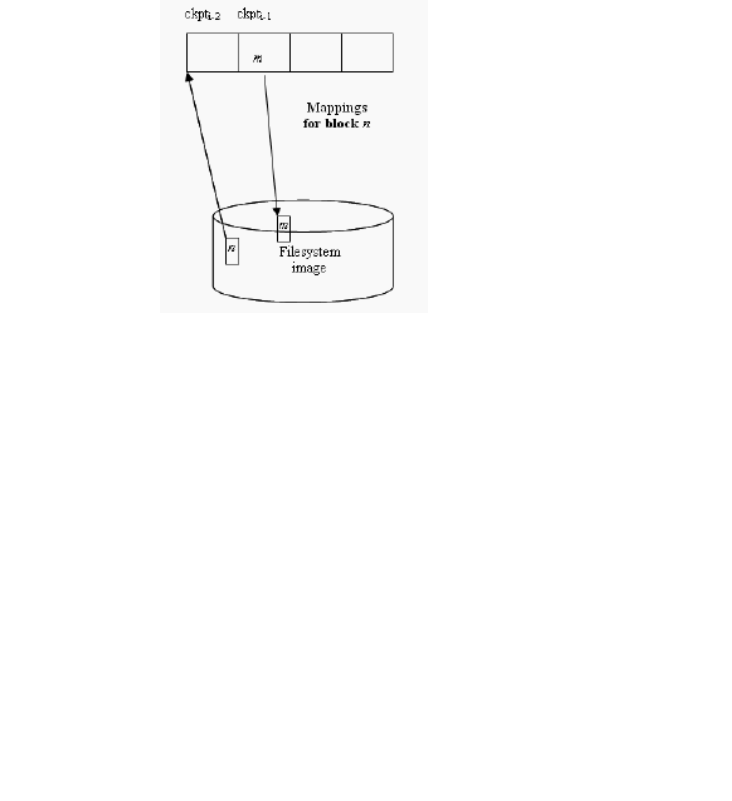
In Figure 6-4, there are two active checkpoints ckpti-2 and ckpti-1. If block n is going
to be modified, a new block m will be allocated and the old content of n is copied to
it. The address for block m will be inserted into the list of mappings for the block n
in the latest checkpoint, which is ckpti-1. From this point, any request for block n in
ckpti-2 and ckpti-1 will be redirected to the block m.
From this, we can tell from a mapping table when system blocks are modified
relative to active checkpoints.
Referring to Figure 6-2, ckpti-2 is created and then without modifying block n -
ckpti-1 is created. Therefore ckpti-2 and ckpti-1 represent the same content for block
n. Before the creation of ckpti, block n had been modified. A copy of the before
change content is made and put into the mapping for the most recent checkpoint
which at that time was ckpti-1. Because both ckpti-1 and ckpti-2 expect to see the
same content for block n, the mapping from n to m is shared by both of them.
FIGURE 6-4 Mappings for Block n After Modification
In Figure 6-2, Ckpti is created and without modifying block n, ckpti+1 is created and
then block n is modified again. This causes the creation of block p and mapping
from n to p for checkpoint ckpti and ckpti+1.
When deleting a block in LFS, the system first checks if there is a mapping for the
block in the most recent checkpoint or not (considering SFS2CP_ALLO_MARKER a
valid mapping). If there is a mapping, it frees the block. Otherwise, it puts the
address of block into the mapping for it, creating a one to one mapping for that
block. This is called page stealing of CFS from LFS.