8-3
Cisco Intrusion Prevention System Appliance and Module Installation Guide for IPS 7.1
OL-24002-01
Chapter 8 Installing and Removing the ASA 5500 AIP SSM
Product Overview
In promiscuous mode, the IPS receives packets over the GigabitEthernet interface, examines them for
intrusive behavior, and generates alerts based on a positive result of the examination. In inline mode,
there is the additional step of sending all packets, which did not result in an intrusion, back out the
GigabitEthernet interface.
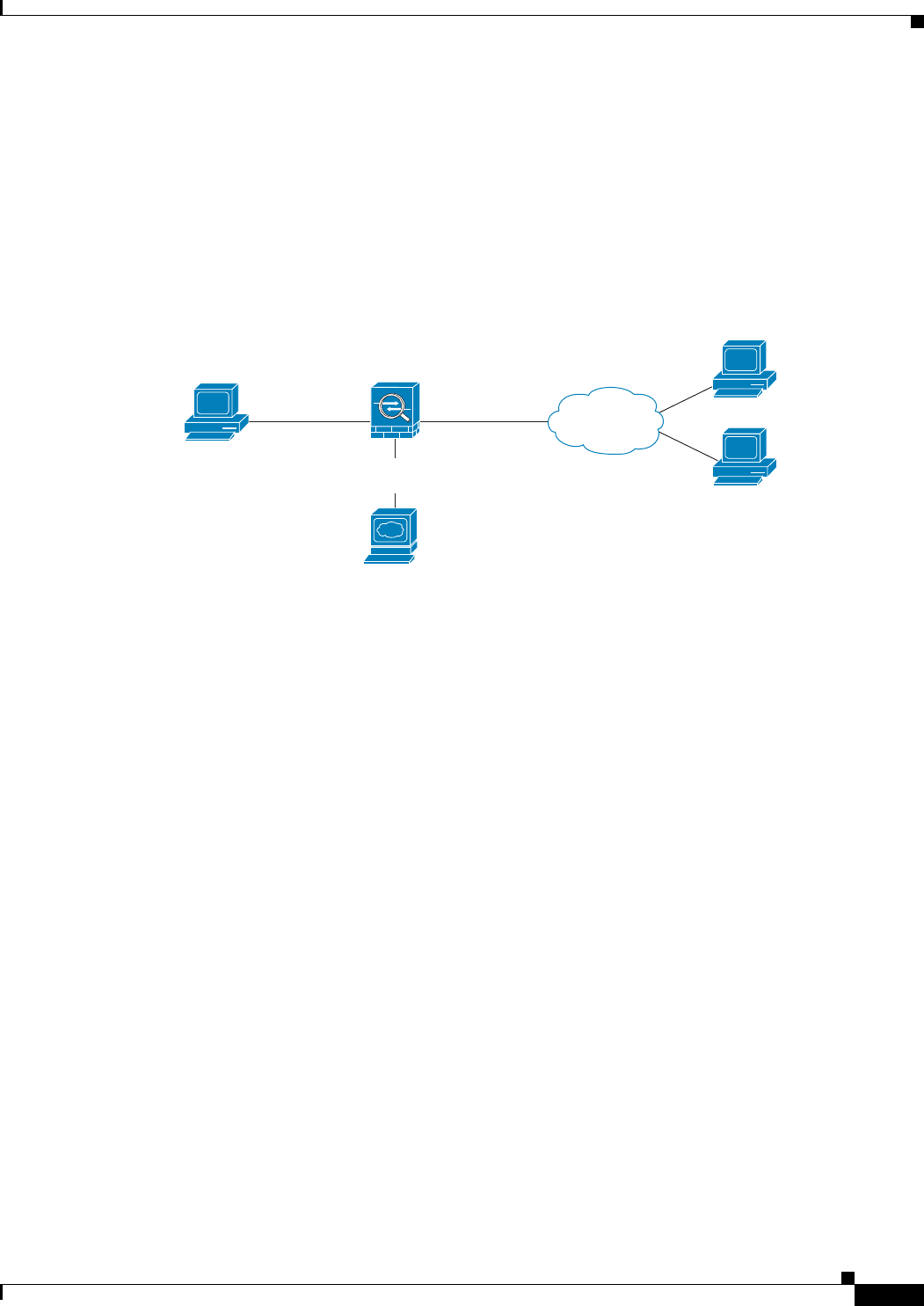
Figure 8-2 shows the adaptive security appliance with the ASA 5500 AIP SSM in a typical DMZ
configuration. A DMZ is a separate network located in the neutral zone between a private (inside)
network and a public (outside) network. The web server is on the DMZ interface, and HTTP clients from
both the inside and outside networks can access the web server securely.
Figure 8-2 DMZ Configuration
In Figure 8-2 an HTTP client (10.10.10.10) on the inside network initiates HTTP communications with
the DMZ web server (30.30.30.30). HTTP access to the DMZ web server is provided for all clients on
the Internet; all other communications are denied. The network is configured to use an IP pool (a range
of IP addresses available to the DMZ interface) of addresses between 30.30.30.50 and 30.30.30.60.
For More Information
•
For more information on setting up the adaptive security appliance, refer to the Getting Started
Guides found at this URL:
http://www.cisco.com/en/US/products/ps6120/prod_installation_guides_list.html
•
For more information on installing the ASA 5500 AIP SSM, see Installing the ASA 5500 AIP SSM,
page 8-5.
•
For more information on configuring the ASA 5500 AIP SSM to receive IPS traffic, refer to
Configuring the ASA 5500 AIP SSM.
148403
Internet
HTTP client
10.10.10.10
Web server
10.30.30.30
DMZ
10.30.30.0
Inside
10.10.10.0
HTTP client
HTTP client
Outside
209.165.200.225
ASA security
appliance


















