176 AT-TQ2403 - Management Software - User's Guide
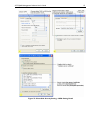
Association Tab
Field Setting
Network Authentication WPA – PSK
Data Encryption TKIP or AES depending on how this option is configured on the
access point.
Note:
When the Cipher Suite on the access point is set to "Both",
then TKIP clients with a valid TKIP key and AES clients with a valid
CCMP (AES) key can associate with the access point
Network Key Provide the key you entered on the access point Security settings
for the cipher suite you are using.
For example, if the key on the access point is set to use a TKIP key
of "012345678", then a TKIP client specify this same string as the
network key.
The key is provided for me
automatically
This box should be disabled automatically based on other settings.
Authentication Tab
Field Setting
Enable IEEE 802.1x
authentication for this
network
Make sure that IEEE 802.1x authentication is disabled (unchecked).
(Setting the encryption mode to WEP should automatically disable
authentication.)
Click OK on the Wireless Network Properties dialog to close it and save your changes.
Connecting to the Wireless Network with a WPA-PSK Client
WPA-PS
K clients should now be able to associate and authenticate with the access point. As a client, you
will not be prompted for a key. The TKIP or AES key you configured on the client security settings is
automatically used when you connect.
Configuring an External RADIUS Server to Recognize the
AT-TQ2403 Wireless Access Point
An external Remote Authentication Dial-in User Server (RADIUS) server running on the network can
support of EAP-TLS smart card/certificate distribution to clients in a Public Key Infrastructure (PKI) as well
as EAP-PEAP user account setup and authentication. By external RADIUS server, we mean an
authentication server external to the access point itself. This is to distinguish between the scenario in
which you use a network RADIUS server versus one in which you use the Built-in Authentication Server on
the AT-TQ2403 Wireless Access Point.
This section provides an example of configuring an external RADIUS server for the purposes of
authenticating and authorizing TLS-EAP certificates from wireless clients of a particular AT-TQ2403
Wireless Access Point configured for either "WPA/WPA2 Enterprise (RADIUS)" or "IEEE 802.1x"
security modes. The intention of this section is to provide some idea of what this process will look like;