AT-TQ2403 Management Software User's Guide 69
If you
have a second client station, that station also needs to have one of the WEP keys defined on the
AP. You could give it the same WEP key you gave to the first station. Or for a more secure solution, you
could give the second station a different WEP key (key 2, for example) so that the two stations cannot
decrypt each other’s transmissions.
Static WEP with Transfer Key Indexes on Client Stations
Some Wireless client software (like Funk Odyssey) lets you configure multiple WEP keys and set a
transfer index on the client station, then you can specify different keys to be used for station-to-AP
transmissions. (The standard Windows wireless client software does not allow you to do this.)
To build on our example, using Funk Odyssey client software you could give each of the clients WEP key
3 so that they can decode the AP transmissions with that key and also give client 1 WEP key 1 and set this
as its transfer key. You could then give client 2 WEP key 2 and set this as its transfer key index.
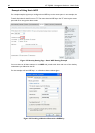
The following figure illustrates the dynamics of the AP and two client stations using multiple WEP keys
and a transfer key index.
Figure 27: Example of Using Multiple WEP Keys and Transfer Key Index on Client
Stations
IEEE 802.1x
IEEE 802.1x is the standard defining port-based authentication and infrastructure for doing key
management. Extensible Authentication Protocol (EAP) messages sent over an IEEE 802.11 wireless
network using a protocol called EAP Encapsulation Over LANs (EAPOL). IEEE 802.1x provides
dynamically-generated keys that are periodically refreshed. An RC4 stream cipher is used to encrypt the
frame body and cyclic redundancy checking (CRC) of each 802.11 frame.
This mode requires the use of a RADIUS server to authenticate users. If the option for the Use
internal RADIUS server is enabled, configure user accounts on the AP via the User Management
tab. Otherwise configure user accounts on the external RADIUS server.
The access point requires a RADIUS server capable of EAP, such as the Microsoft Internet
Authentication Server or the AT-TQ2403 Management Software internal authentication server. To
work with Windows clients, the authentication server must support Protected EAP (PEAP) and
MSCHAP V2.
When configuring IEEE 802.1x mode, you have a choice of whether to use the embedded RADIUS
server or an external RADIUS server that you provide. The AT-TQ2403 Management Software
embedded RADIUS server supports Protected EAP (PEAP) and MSCHAP V2.
If you use your own RADIUS server, you have the option of using any of a variety of authentication
methods that the IEEE 802.1x mode supports, including certificates, Kerberos, and public key
authentication. Keep in mind, however, that the client stations must be configured to use the same
authentication method being used by the access point.