Configuring Rights
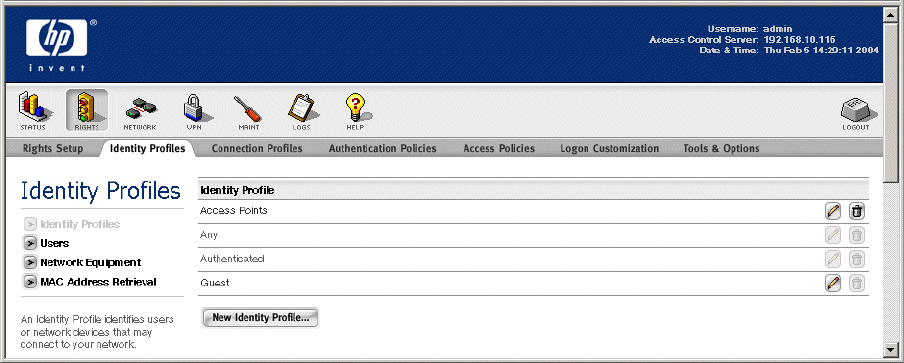
Figure 4-4. The Identity Profiles Page
The 700wl Series system provides three predefined Identity Profiles, and a Rights Administrator can
create additional ones. The predefined Identity Profiles can be considered default or implicit profiles, as
users will match them automatically based on certain criteria.
The predefined Identity Profiles are:
• Authenticated: clients that have been successfully authenticated automatically match this profile
• Guest: clients that log on through the Guest logon feature automatically match this profile (Guests are
not considered authenticated)
• Access Points: clients (identified by MAC address) that are actually Access Points
• Any: all clients automatically match this profile
These predefined profiles are typically used in rows at the bottom of the Rights Assignment Table, to
catch clients that do not match more specific Identity Profiles higher in the table. If you plan to use these
profiles in combination with other Identity Profiles you create, it is important that you order your rows
correctly so that the more specific Identity Profile will be evaluated first.
» To edit an Identity Profile, click the Identity Profile name in the first column of the table, or click the
pencil icon at the end of the row. You cannot edit the Authenticated or Any profile.
» To delete an Identity Profile, click the trash can icon at the end of the row. You cannot delete the
predefined Identity Profiles.
» To create a new Identity Profile, click the New Identity Profile... button at the bottom of the Identity
Profiles list. This takes you to the New Identity Profile page
You can use the links directly under the page name in the left-hand panel of the page to go directly to the
Users or Network Equipment pages to view lists of users and network equipment in the built-in database.
You can also access the setup page to configure the automatic retrieval of MAC addresses from an LDAP
database for inclusion in the built-in database. See
“Users in the Built-In Database” on page 4-16,
“Network Equipment in the Built-in Database” on page 4-20, or “Retrieving MAC Addresses from an
LDAP Database” on page 4-24 for details on these functions.
4-12 HP ProCurve Secure Access 700wl Series Management and Configuration Guide