Chapter 23 - Ultra Secure Mode
Polycom, Inc. 23-55
Non-hashed Passwords
All non-hashed passwords are stored encrypted as set out in Table 23-17.
Downgrade
from new
version to old
version
Before the downgrade procedure
begins, the administrator receives a
popup warning message “Passwords
will change to factory default would
you like to proceed?”
All users and SHA-256 hashed
passwords are deleted.
The administrator’s User Name and
Password reverts to the Factory
Default: POLYCOM / POLYCOM.
The old version accepts certificates
issued with SHA-1 hashing.
For certificates issued with SHA-256
hashing:
• The administrator receives a popup
warning message "TLS certificate
will be deleted and the system will
switch to non-secured connection,
would you like to proceed?”
• For each certificate that is hashed
with SHA-256:
• RMX Web Client / RMX
Manager connections to the
RMX are switched to non-
secured mode.
• LDAP services are changed
from 636 to port 389.
• SIP TLS sessions are changed
to SIP UDP.
• The certificate is deleted.
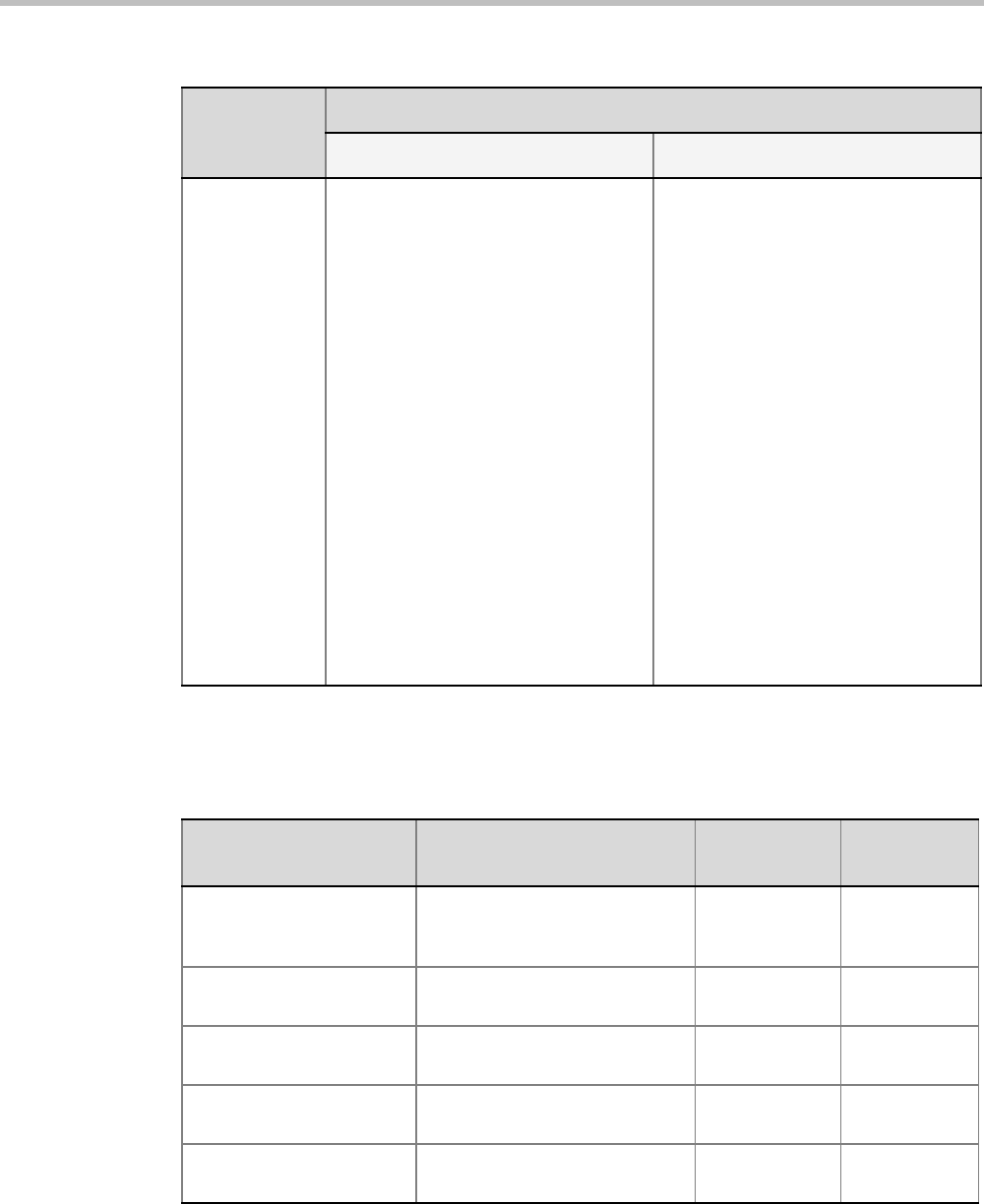
Table 23-17 Non-hashed Passwords - Encryption
Connection Storage type
Previous
Versions
From
Version 8.1
SNMPv3
Two passwords:
Authentication / Privacy
Community permissions which
are not the PW to connect to
SNMP are not Saved Encrypted
Non encrypted AES 256
Exchange Non encrypted – Feature
disabled in Ultra Secure Mode
Non encrypted AES 256
RV v.35 serial ports –
password for login
Reversible – AES_128 with 256
Bytes Key (2048 Bits)
AES 256 AES 256
H.323 authentication –
password
Reversible – AES_128 with 256
Bytes Key (2048 Bits)
AES 256 AES 256
SIP digest – password Reversible – AES_128 with 256
Bytes Key (2048 Bits)
AES 256 AES 256
Table 23-16 Version Change - Password and Certificate Compatibility (Continued)
Version
Change
Behavior
Passwords Certificates


















