VPDN and L2TP Overview 605
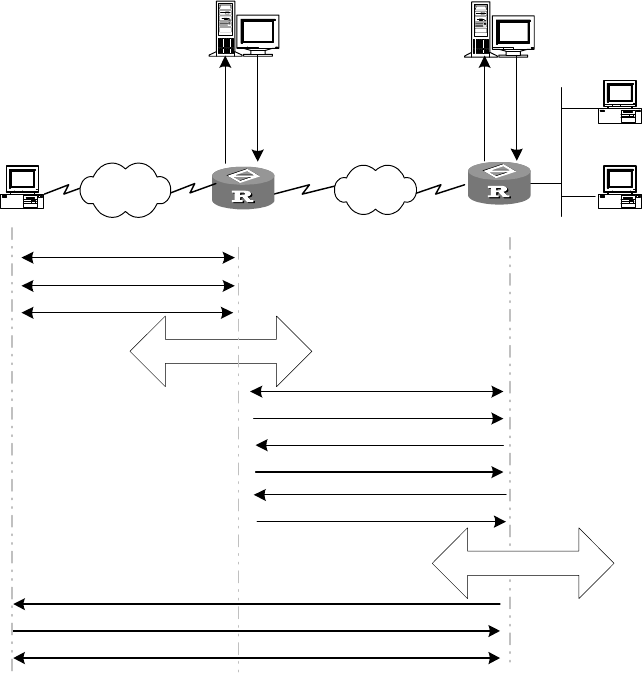
Figure 182 Call setup flow of L2TP channel
V. Features of L2TP
■ Flexible identity authentication mechanism and high security
L2TP protocol by itself does not provide connection security, but it can depend
on the authentication (e.g. CHAP and PAP) provided by PPP, so it has all security
features of PPP. L2TP can be integrated with IPSec to fulfill data security, so it is
difficult to attack the data transmitted with L2TP. As required by specific
network security, L2TP adopts channel encryption technique, end-to-end data
encryption or application layer data encryption on it to improve data security.
■ Multi-protocol transmission
L2TP transmits PPP packets, so multiple protocols can be encapsulated in
PPP packets.
■ Supports the authentication of RADIUS server
LAC requires the authentication of RADIUS with user name and password.
RADIUS server receives authentication request of the user, fulfils the
authentication and returns the configuration information to establish the
connection to LAC.
■ Supports internal address allocation
LNS can be put behind the Intranet firewall. It can dynamically distribute and
manage the addresses of remote users and support the application of private
WAN
PSTN/ISDN
RADIUS Server RADIUS Server
Access request
(12)(16)
Access response
(13)(17)
(12)
(16)
(13)
(17)
LAC
LNS
(5) AV Pairs
Tunnel messae(
(4) Request
tunnl message
PC
PC
PC
Router A
Router B
Call Setup
(1)
PPP LCP Setup
(2)
PAP or
CHAP authentication
(3)
(6) Tunnel establishment
(7) SCCRQ message [ LAC challenge ]
SCCRP message [ LNS CH AP response, CHAP challenge ]
(9) SCCCN message [ Authentication passes£¬LAC CHAP response ]
(10) Authentication passes)
user CHAP response + response identifier + PPP negotiation parameters
(11)
(8)
14) Optional second time
CHAP challenge(
(15) CHAP response
(18) Authentication passes
RADIUS Aut hent i cat i on
RADIUS Aut henti cat i on


















