630 CHAPTER 43: CONFIGURING L2TP
[Router2] ip pool 1 192.168.0.2 192.168.0.100
b Enable AAA authentication.
[Router2] aaa-enable
[Router2] aaa authentication-scheme ppp default local
c Configure Virtual-Template 1.
[Router2] interface virtual-template 1
[Router2-Virtual-Template1] ip address 192.168.0.1 255.255.255.0
[Router2-Virtual-Template1] ppp authentication-mode chap
[Router2-Virtual-Template1] remote address pool 1
d Configure a L2TP group and the related attributes.
[Router2] l2tp enable
[Router2] l2tp-group 1
[Router2-l2tp1] tunnel name lns-end
[Router2-l2tp1] allow l2tp virtual-template 1 remote lac-end
e Configure the username and password that are the same as those configured
at the LAC side.
[Router2] local-user vpdnuser@3Com.com password simple Hello
f Enable tunnel authentication and configure the tunnel authentication
password to
3Com.
[Router2-l2tp1] tunnel authentication
[Router2-l2tp1] tunnel password simple 3Com router
g Force to implement local CHAP authentication.
[Router2-l2tp1] mandatory-chap
Networking of VPN
Protected by IPSec
I. Networking requirements
To create an IPSec tunnel between the both ends of L2TP to transmit L2TP packets
which are encrypted through IPSec, so as to guarantee the security for VPN.
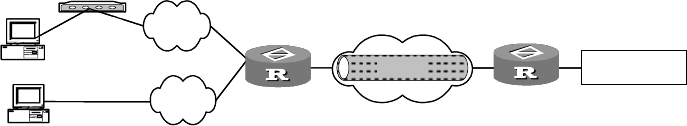
II. Networking diagram
Figure 197 Networking of VPN protected by IPSec
III. Procedures
1 Configuration at the user side
Set up a dialup network whose number is the access number of Router1, and it
receives the IP address assigned by the LNS server. Input “vpdnuser” as the
username and “Hello” as the password in the dialup terminal window.
2 Configuration at Router1 (LAC side)
a Configure the username and password.
[Router1] local-user vpdnuser password simple Hello
Internet
Tunnel
WAN
PSTN
ISDN
PC1
PC2
LAC
Quidway1
LNS
Quidway2
Modem
Company
headquarters
IPSec
encryption tunnel
Internet
Tunnel
WAN
PSTN
ISDN
PC1
PC2
LAC
Quidway1
LNS
Quidway2
Modem
Company
headquarters
IPSec
encryption tunnel
Router1
Router2
Headquarters
