668 CHAPTER 48: TRAFFIC POLICING, TRAFFIC SHAPING AND LINE RATE
■ Dropping directly — CAR drops the packets that do not "conform to" the
traffic specifications.
■ Forwarding after modifying the packet priority level — The packets with the
estimated result of "partial conformance" are forwarded after they are marked
as the lower priority level flows.
■ Entering the next level of policing — Traffic policing may be stacked level by
level, and each level concerns and polices more specific targets. A downstream
network can receive the estimated result from an upstream network, or it can
be classified according to its own standard.
Traffic policing uses the Token Bucket algorithm, and each service has tokens
which are transmitted at a specified rate. If the reaching speed of the user packets
is faster than the speed at which the tokens are transmitted, it is necessary to take
measures for the data exceeding the specified rate, for example, they are marked
and allowed to pass through the network only when the network is not congested
and they are dropped first when the network is congested. These data packets can
also be dropped directly, which is completely dependent on the agreement and
rules between the operators and users.
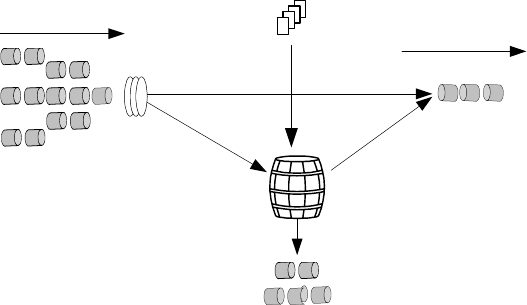
Token bucket feature The token bucket may be regarded as a container that
stores tokens. The system puts tokens into the bucket at the set speed. When the
bucket is full of tokens, the excessive tokens overflow, and the number of the
tokens in the bucket does not increase.
Figure 210 Schematic diagram of packet line classification and traffic policing
Measuring the traffic by the token bucket Evaluating the traffic specification
by the token bucket is based on whether the number of the tokens in the token
bucket is enough for packet forwarding. If the bucket has sufficient tokens to
forward packets, the traffic does not exceed the specification, otherwise, it
exceeds the specification. Usually, one token is associated with one bit of
forwarding authority.
Three main parameters are used in the evaluation of the traffics:
■ Time Interval: Evaluates the traffic in every other period. This parameter is set
by the system. For every evaluation, if the bucket has sufficient tokens to be
used by one or more packets, it is considered “in conformance”. If the bucket
incoming packets
outgoing packets
Token Bucket
Tokens enter bucket
at the given speed
classify
Discarded
packets


















