802.1X | 123
Multi-Host Authentication
Multi-Host Authentication is available on platforms: c e
t
s
802.1x assumes that a single end-user is connected to a single authenticator port, as shown in Figure 7-15;
this one-to-one mode of authentication is called Single-host mode. If multiple end-users are connected to
the same port, a many-to-one configuration, only the first end-user to respond to the identity request is
authenticated. Subsequent responses are ignored, and a system log is generated to indicate reception of
unexpected 802.1x frames. When a port is authorized, the authenticated supplicant MAC address is
associated with the port, and traffic from any other source MACs is dropped.
Figure 7-15. Single-host Authentication Mode
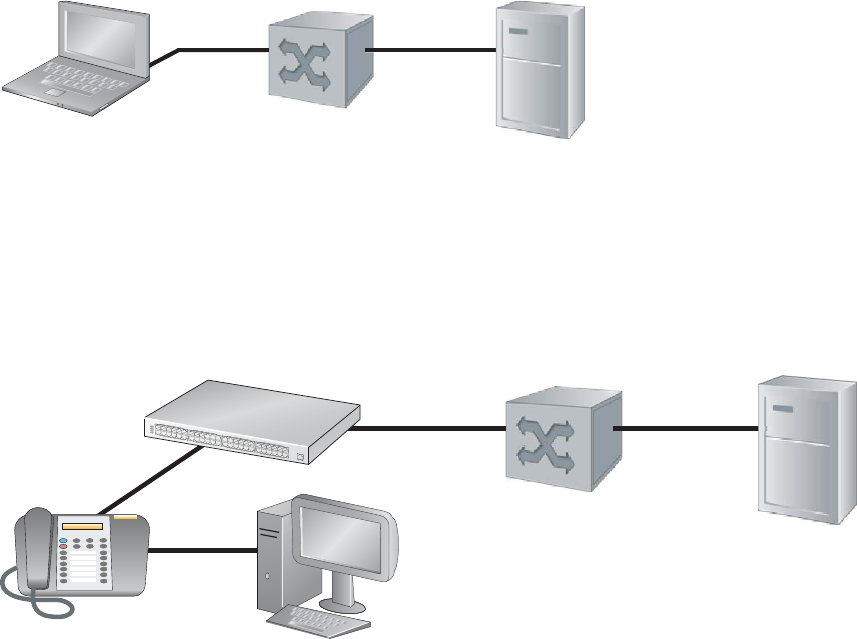
When multiple end-users are connected to a single authenticator port, Single-host mode authentication
does not authenticate all end-users, and all but one are denied access to the network. For these cases
(Figure 7-16), FTOS offers Multi-host mode authentication.
Figure 7-16. Multi-host Authentication Mode
When Multi-host mode authentication is configured, the first client to respond to an identity request is
authenticated, and subsequent responses are still ignored, but since the authenticator expects the possibility
of multiple responses, no system log is generated. After the first supplicant is authenticated, all end-users
attached to the authorized port are allowed to access the network.
If the authorized port becomes unauthorized due to re-authentication failure or the supplicant sends an
EAPOL logoff frame, all attached end-users are denied access to the network.
End-user Device
Force10 switch
RADIUS Serv
er
EAP over LAN (EAPOL)
EAP over RADIUS
End-user Devices
Force10 switch
RADIUS Serv
er
EAP over LAN (EAPOL)
EAP over RADIUS


















