Customizing the Data Protector Environment
Firewall Support
Chapter 11 535
Examples of Configuring Data Protector in Firewall
Environments
The following section provides examples on how to configure Data
Protector in four different firewall environments.
Example 1: Disk Agent and Media Agent Installed Outside, Other
Components Installed Inside a Firewall
You can configure your backup environment so that the Cell Manager
and GUI are in the intranet and some Disk Agents and Media Agents are
in the Demilitarized Zone (DMZ):
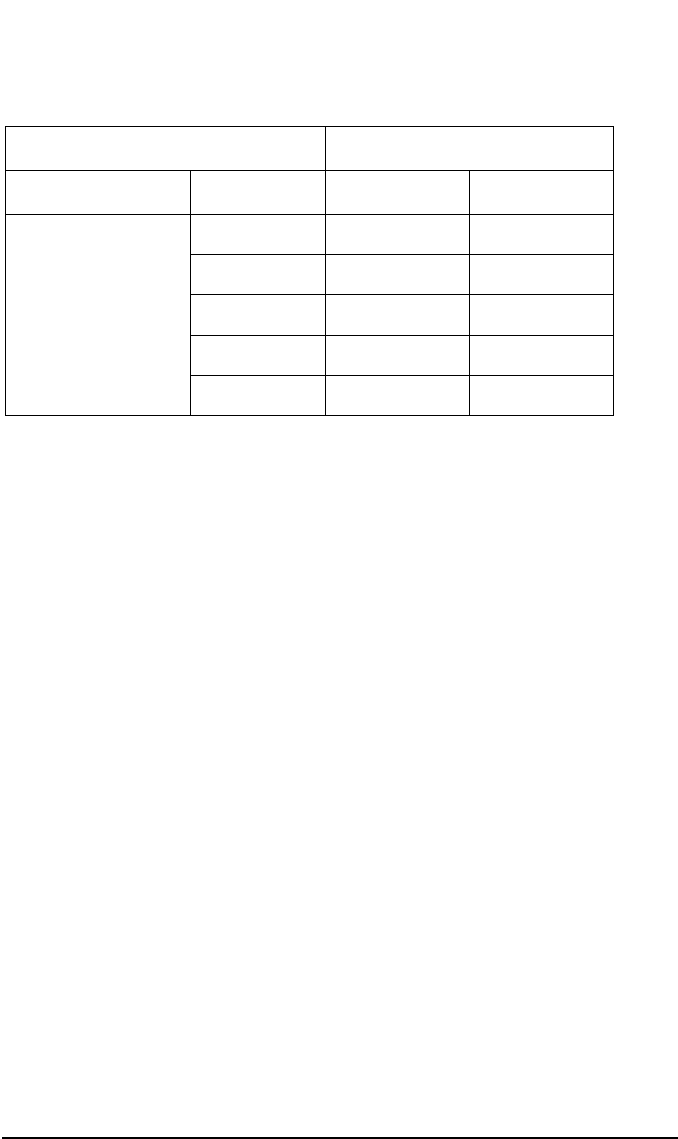
Application Agent
N/A
a
Inet on CM 5555
N/A
a
CRS Dynamic
N/A
a
RSM Dynamic
N/A
a
BSM Dynamic
N/A
a
xMA-NET Dynamic
a. The source port of a connection is always assigned by
the operating system and cannot be limited to a specific
range.
b. To be more precise, it is the Inet process that accepts
the connection on port 5555 and then starts the
requested agent process. The agent process inherits the
connection.
c. This applies only to the MMD on the system running
the CMMDB in a Manager-of-Managers (MoM)
environment.
d. Only for backup sessions with the reconnect feature
enabled.
e. Connections to the Utility Media Agent (UMA) are only
required when sharing a library across several
systems.
Table 11-3
Connecting Component Listening Component
Process Port Process Port


















