29-7
Cisco ASDM User Guide
OL-16647-01
Chapter 29 Configuring Trend Micro Content Security
Managing the CSC SSM
You enable traffic scanning with the CSC SSM on the CSC Scan tab in the Add Service Policy Rule
Wizard Rule Actions screen. You can apply service policies that include CSC scanning globally or to
specific interfaces; therefore, you can choose to enable CSC scans globally or for specific interfaces. For
more information, see Rule Actions for CSC Scanning, page 29-8.
Adding the csc command to your global policy ensures that all unencrypted connections through the
adaptive security appliance are scanned by the CSC SSM; however, this setting may cause traffic from
trusted sources to be scanned unnecessarily.
If you enable CSC scans in interface-specific service policies, these scans are bi-directional.
Bi-directional scanning means that when the adaptive security appliance opens a new connection, if CSC
scanning is active on either the inbound or the outbound interface of that connection and the service
policy identifies traffic for scanning, the adaptive security appliance diverts this traffic to the CSC SSM.
Bi-directional scanning also means that if you divert any of the supported traffic types that cross a given
interface to the CSC SSM, unnecessary scanning may be occurring on traffic from your trusted inside
networks. For example, URLs and files requested from web servers on a DMZ network are unlikely to
pose content security risks to hosts on an inside network, and you probably do not want the adaptive
security appliance to divert such traffic to the CSC SSM.
Therefore, we highly recommend that the service policies to define CSC scans use access lists to limit
the selected traffic. Specifically, use access lists that match the following:
• HTTP connections to outside networks.
• FTP connections from clients inside the adaptive security appliance to servers outside the adaptive
security appliance.
• POP3 connections from clients inside the adaptive security appliance to servers outside the adaptive
security appliance.
• Incoming SMTP connections destined to go to inside mail servers.
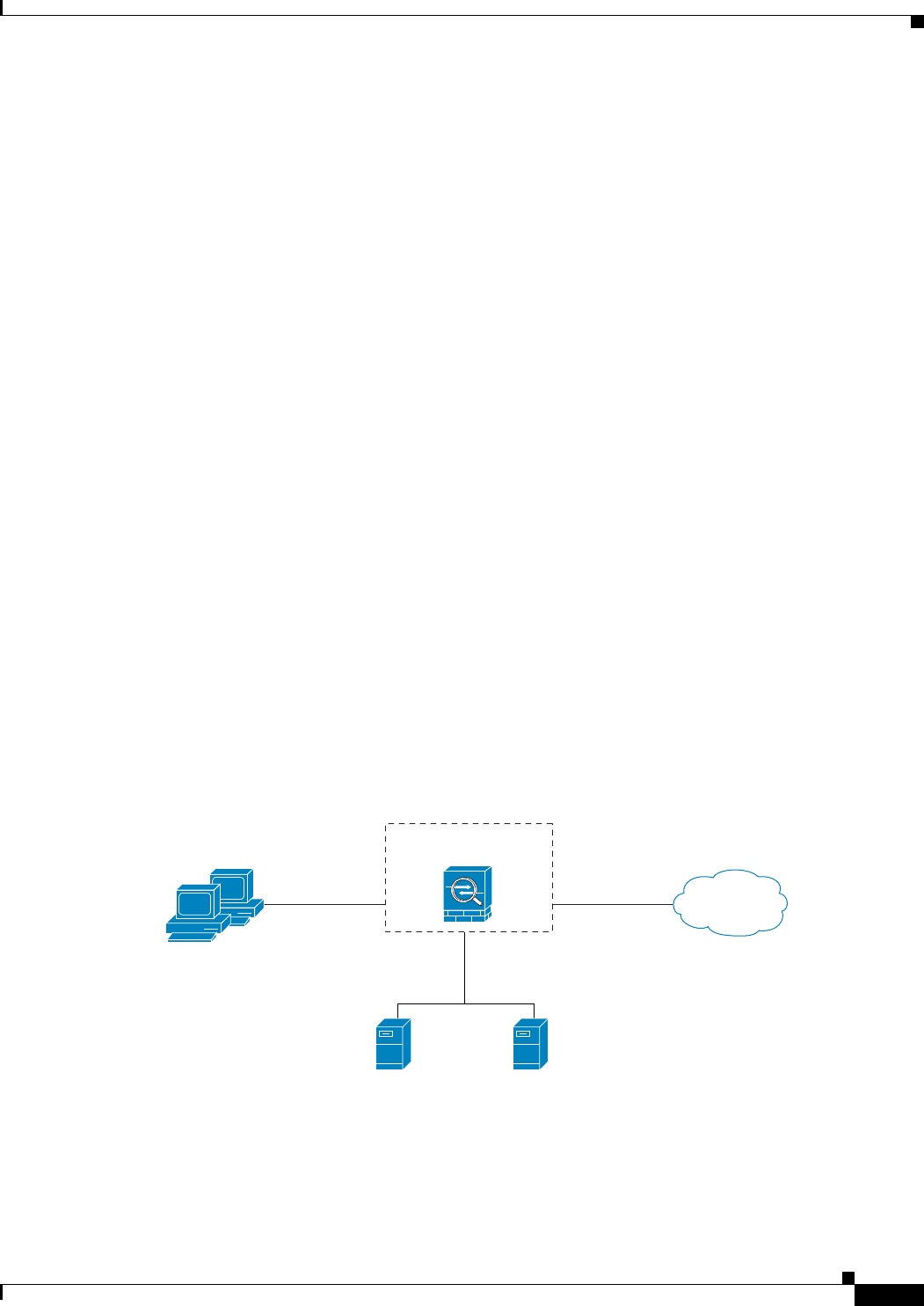
In Figure 29-3, you should configure the adaptive security appliance to divert traffic to CSC SSM
requests from clients on the inside network for HTTP, FTP, and POP3 connections to the outside network
and incoming SMTP connections from outside hosts to the mail server on the DMZ network. You should
not enable scanning of HTTP requests from the inside network to the web server on the DMZ network.
Figure 29-3 Common Network Configuration for CSC SSM Scanning
There are many ways you could configure the adaptive security appliance to identify the traffic that you
want to scan. One approach is to define two service policies: one on the inside interface and the other on
the outside interface, each with access lists that match traffic to be scanned.
192.168.30.0
192.168.20.0
(dmz)
Web server Mail server
192.168.10.0
Internet
outside inside
Security
appliance
143800


















