29-8
Cisco ASDM User Guide
OL-16647-01
Chapter 29 Configuring Trend Micro Content Security
Managing the CSC SSM
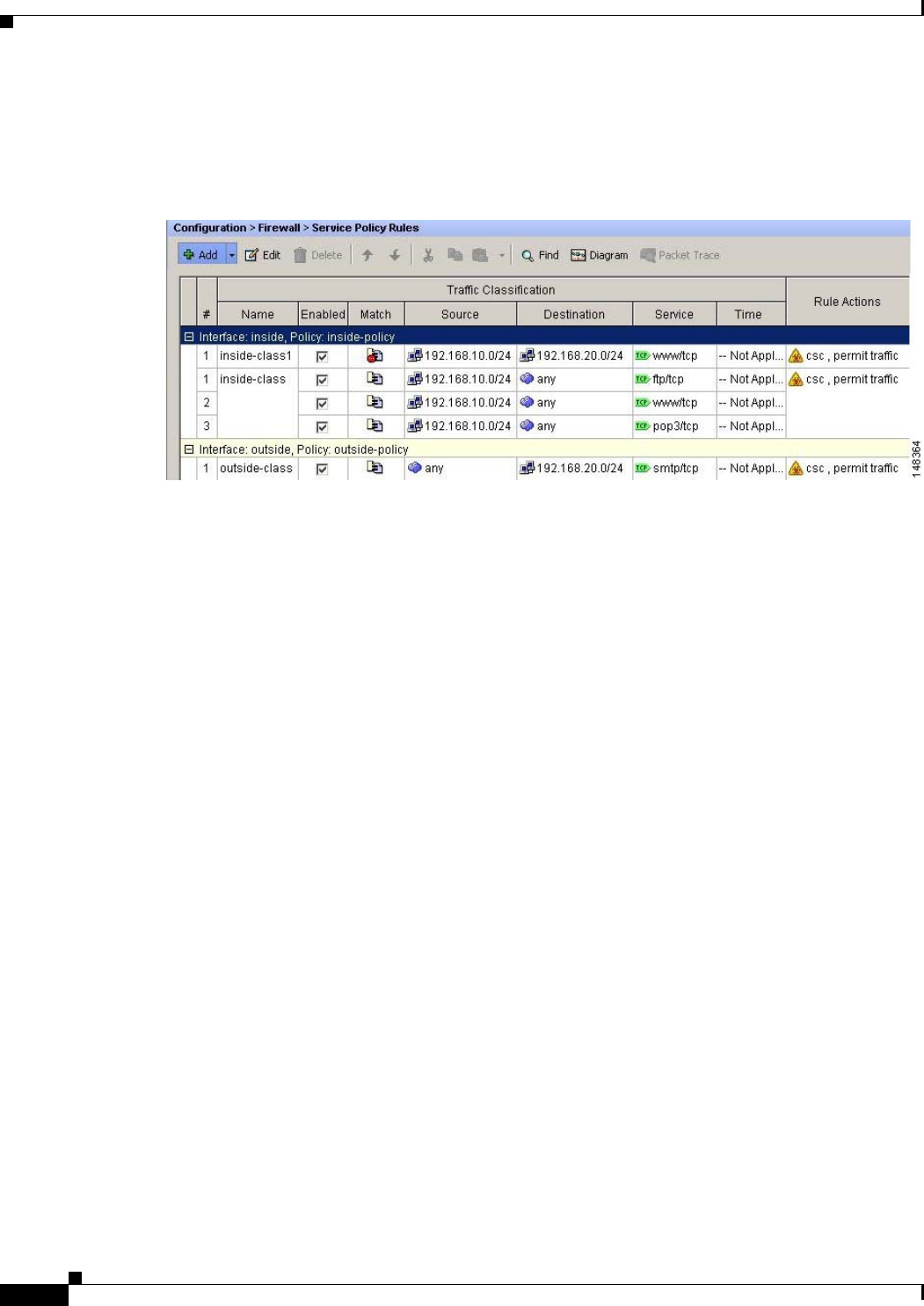
Figure 29-4 shows service policy rules that select only the traffic that the adaptive security appliance
should scan.
Figure 29-4 Optimized Traffic Selection for CSC Scans
In the inside-policy, the first class, inside-class1, ensures that the adaptive security appliance does not
scan HTTP traffic between the inside network and the DMZ network. The Match column indicates this
setting by displaying the “Do not match” icon. This setting does not mean the adaptive security appliance
blocks traffic sent from the 192.168.10.0 network to TCP port 80 on the 192.168.20.0 network. Instead,
this setting exempts the traffic from being matched by the service policy applied to the inside interface,
which prevents the adaptive security appliance from sending the traffic to the CSC SSM.
The second class of the inside-policy, inside-class matches FTP, HTTP, and POP3 traffic between the
inside network and any destination. HTTP connections to the DMZ network are exempted because of the
inside-class1 setting. As previously mentioned, policies that apply CSC scanning to a specific interface
affect both incoming and outgoing traffic, but by specifying 192.168.10.0 as the source network,
inside-class1 matches only connections initiated by the hosts on the inside network.
In the outside-policy, outside-class matches SMTP traffic from any outside source to the DMZ network.
This setting protects the SMTP server and inside users who download e-mail from the SMTP server on
the DMZ network, without having to scan connections from SMTP clients to the server.
If the web server on the DMZ network receives files uploaded by HTTP from external hosts, you can add
a rule to the outside policy that matches HTTP traffic from any source to the DMZ network. Because the
policy is applied to the outside interface, the rule would only match connections from HTTP clients
outside the adaptive security appliance.
Rule Actions for CSC Scanning
The CSC Scan tab lets you determine whether the CSC SSM scans traffic identified by the current traffic
class. This tab appears only if a CSC SSM is installed in the adaptive security appliance.
The CSC SSM scans only HTTP, SMTP, POP3, and FTP traffic. If your service policy includes traffic
that supports other protocols in addition to these four, packets for other protocols are passed through the
CSC SSM without being scanned. To reduce the load on the CSC SSM, configure the service policy rules
that send packets to the CSC SSM to support only HTTP, SMTP, POP3, or FTP traffic.
Fields
• Enable CSC scan for this traffic flow—Enables or disables use of the CSC SSM for this traffic flow.
When this check box is checked, the other parameters on this tab become active.


















