34-22
Cisco ASDM User Guide
OL-16647-01
Chapter 34 IKE
Setting Global NAC Parameters
Step 2 Add an entry for each of your security appliance outside interfaces into your DNS server, if such entries
are not already present. Each security appliance outside IP address should have a DNS entry associated
with it for lookups. These DNS entries must also be enabled for Reverse Lookup.
Step 3 Enable DNS lookups on your security appliance on the dialog box Configuration > Device
Management > DNS > DNS Client for whichever interface has a route to your DNS server.
Step 4 Define your DNS server IP address on the security appliance. To do this, click Add on this dialog box.
This opens the Add DNS Server Group dialog box. Enter the IP address of the DNS server you want to
add; for example,
192.168.1.1 (IP address of your DNS server).
Step 5 Click OK and Apply.
Modes
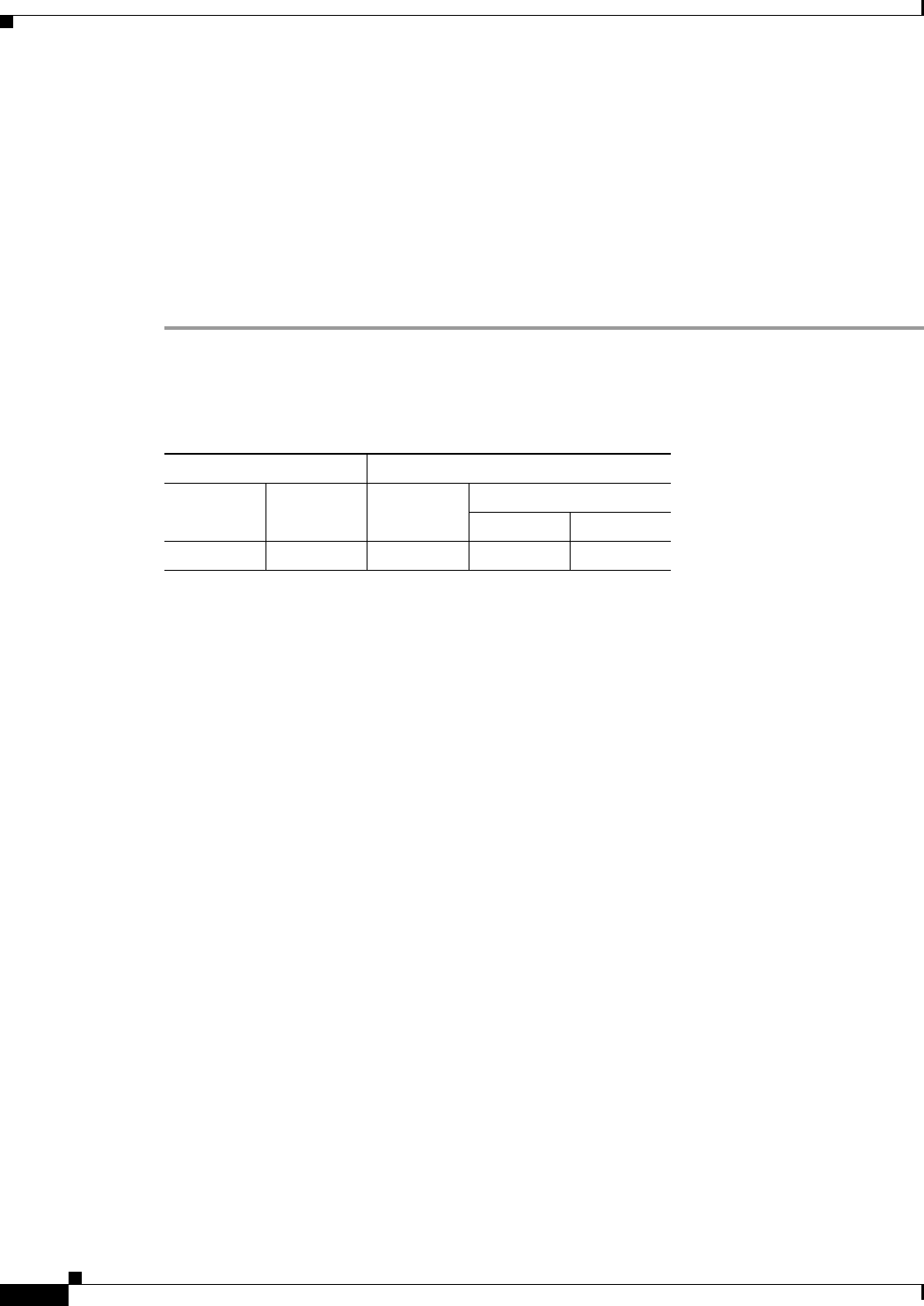
The following table shows the modes in which this feature is available:
Setting Global NAC Parameters
The security appliance uses Extensible Authentication Protocol (EAP) over UDP (EAPoUDP)
messaging to validate the posture of remote hosts. Posture validation involves the checking of a remote
host for compliancy with safety requirements before the assignment of a network access policy. An
Access Control Server must be configured for Network Admission Control before you configure NAC
on the security appliance.
Fields
The NAC window lets you set attributes that apply to all NAC communications. The following global
attributes at the top of the window apply to EAPoUDP messaging between the security appliance and
remote hosts:
• Port—Port number for EAP over UDP communication with the Cisco Trust Agent (CTA) on the
host. This number must match the port number configured on the CTA. Enter a value in the range
1024 to 65535. The default setting is 21862.
• Retry if no response—Number of times the security appliance resends an EAP over UDP message.
This attribute limits the number of consecutive retries sent in response to Rechallenge Interval
expirations. The setting is in seconds. Enter a value in the range 1 to 3. The default setting is 3.
• Rechallenge Interval—The security appliance starts this timer when it sends an EAPoUDP message
to the host. A response from the host clears the timer. If the timer expires before the security
appliance receives a response, it resends the message. The setting is in seconds. Enter a value in the
range 1 to 60. The default setting is 3.
• Wait before new PV Session—The security appliance starts this timer when it places the NAC
session for a remote host into a hold state. It places a session in a hold state if it does not receive a
response after sending EAPoUDP messages equal to the value of the “Retry if no response” setting.
The security appliance also starts this timer after it receives an Access Reject message from the ACS
Firewall Mode Security Context
Routed Transparent Single
Multiple
Context System
• — • ——


















