613
APPENDIX B Instructions
Note:
m: RW0 value (counter value), n: Loop count
See Table B.5-1 and Table B.5-2 for information on (a) to (d) in the table.
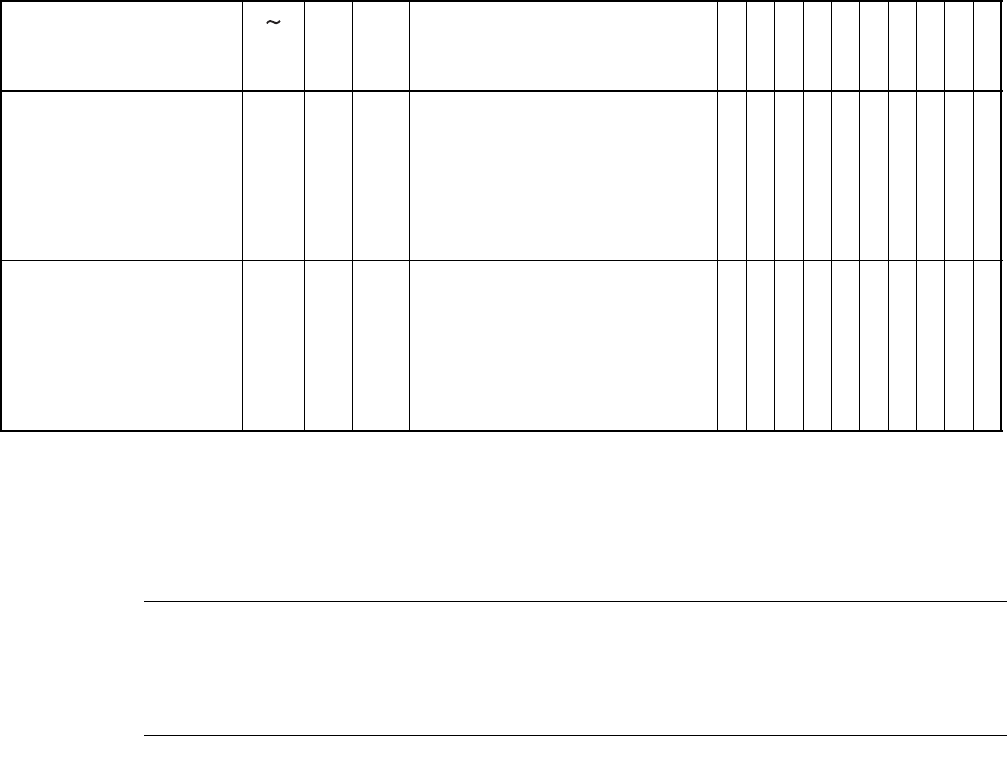
Table B.8-18 10 String Instructions
Mnemonic # RG B Operation L
H
A
H
I STNZVCR
M
W
MOVS / MOVSI 2 *2 *5 *3 byte transfer @AH+ <-- @AL+, counter = RW0 - - --------
MOVSD 2 *2 *5 *3 byte transfer @AH- <-- @AL-, counter = RW0 - - --------
SCEQ / SCEQI 2 *1 *5 *4 byte search @AH+ <-- AL, counter RW0 - - -- -****-
SCEQD 2 *1 *5 *4 byte search @AH- <-- AL, counter RW0 -- -- -****-
FILS / FILSI 2 6m+6 *5 *3 byte fill @AH+ <-- AL, counter RW0 - - ---**---
MOVSW / MOVSWI 2 *2 *5 *6 word transfer @AH+ <-- @AL+, counter = RW0 ----------
MOVSWD 2 *2 *5 *6 word transfer @AH- <-- @AL-, counter = RW0 ----------
SCWEQ / SCWEQI 2 *1 *5 *7 word search @AH+ - AL, counter = RW0 -- -- -****-
SCWEQD 2 *1 *5 *7 word search @AH- - AL, counter = RW0 - - -- -****-
FILSW / FILSWI 2 6m+6 *5 *6 word fill @AH+ <-- AL, counter = RW0 - - ---**---
*1: 5 when RW0 is 0, 4 + 7 x (RW0) when the counter expires, or 7n + 5 when a match occurs
*2: 5 when RW0 is 0; otherwise, 4 + 8 x (RW0)
*3: (b) x (RW0) + (b) x (RW0) When the source and destination access different areas, calculate the (b) item individually.
*4: (b) x n
*5: 2 x (RW0)
*6: (c) x (RW0) + (c) x (RW0) When the source and destination access different areas, calculate the (c) item individually.
*7: (c) x n


















