2-30 PPC405 Core User’s Manual
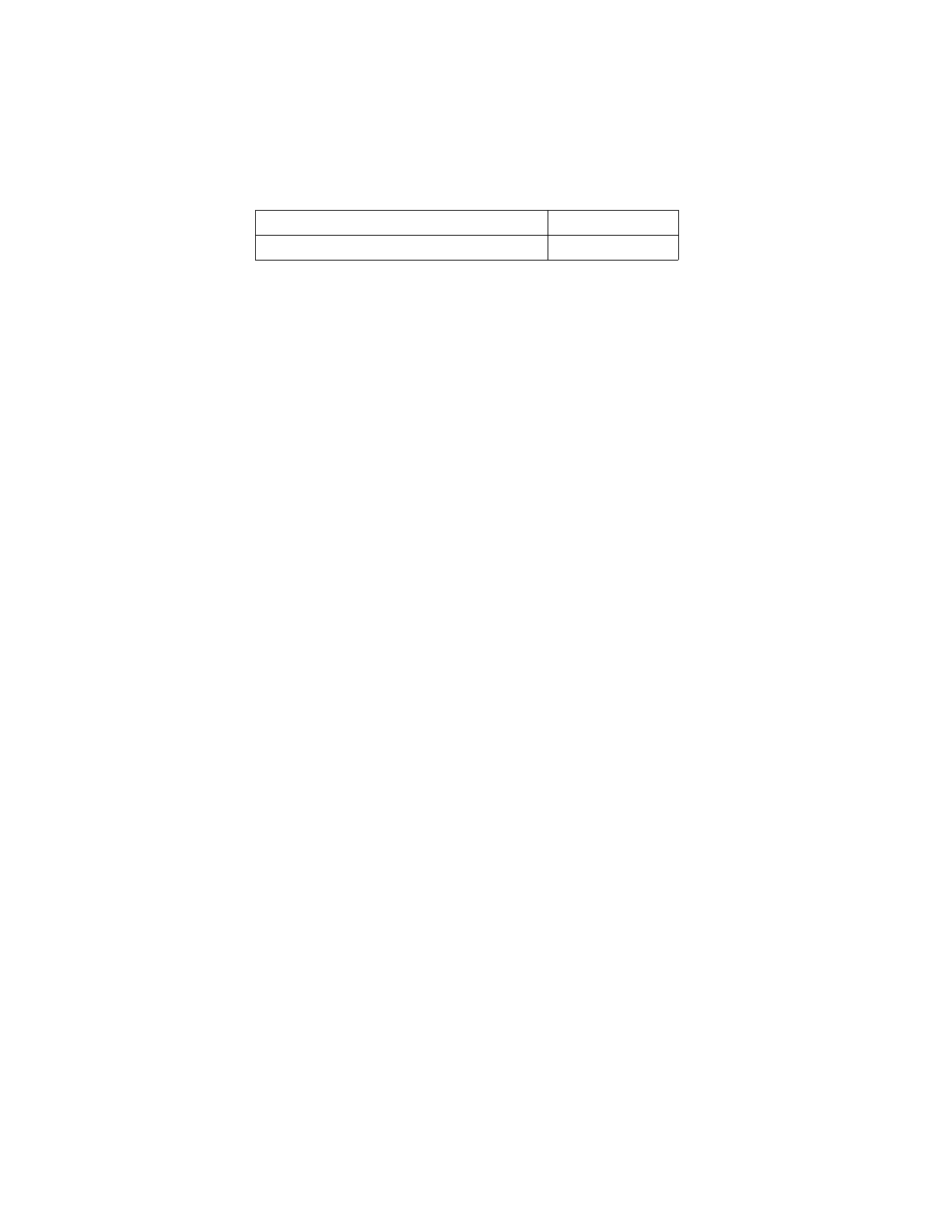
Table 2-8 shows two address regions of the PPC405 core. Suppose a system designer can map all
I/O devices and all ROM and SRAM devices into any location in either region. The choices made by
the designer can prevent speculative accesses to the memory-mapped I/O devices.
A simple way to avoid the problem of speculative reads to peripherals is to map all storage containing
code into Region 2, and all I/O devices into Region 1. Thus, accesses to Region 2 would only be for
code and program data. Speculative fetches occuring in Region 2 would never access addresses in
Region 1. Note that this hardware organization eliminates the need to use of the G storage attribute to
protect Region 1. However, Region 1 could be set as guarded with no performance penalty, because
there is no code to execute or variable data to access in Region 1.
The use of these regions could be reversed (code in Region 1 and I/O devices in Region 2), if Region
2 is set as guarded. Prefetching from the highest addresses of Region 1 could cause an attempt to
speculatively access the bottom of Region 2, but guarding prevents this from occurring. The
performance penalty is slight, under the assumption that code infrequently executes the instructions
in the highest addresses of Region 1.
2.8.3 Summary
Software should take the following actions to prevent speculative accesses to sensitive data areas, if
the sensitive data areas are not in guarded storage:
• Protect against accesses to “random” values in the LR or CTR on blr or bctr branches following rfi,
rfci, or sc instructions by putting appropriate instructions before or after the rfi, rfci, or sc
instruction. See “Fetching Past an Interrupt-Causing or Interrupt-Returning Instruction” on
page 2-28.
• Protect against “running past” the end of memory into a bordering I/O device by putting an
unconditional branch at the end of the memory area. See “Fetching Past an Unconditional Branch”
on page 2-29.
• Recognize that a maximum of 19 words can be prefetched past an unresolved conditional branch,
either down the target path or the sequential path. See “Prefetch Distance Down an Unresolved
Branch Path” on page 2-28.
Of course, software should not code branches with known unsafe targets (either relative to the
instruction counter, or to addresses contained in the LR or CTR), on the assumption that the targets
are “protected” by code guaranteeing that the unsafe direction is not taken. The fetcher assumes that
if a branch is predicted to be taken, it is safe to fetch down the target path.
2.9 Privileged Mode Operation
In the PowerPC Architecture, several terms describe two operating modes that have different
instruction execution privileges. When a processor is in “privileged mode,” it can execute all
instructions in the instruction set. This mode is also called the “supervisor state.” The other mode, in
Table 2-8. Example Memory Mapping
0x7800 0000 – 0x7FFF FFFF (SGR bit 15) 128MB Region 2
0x7000 0000 – 0x77FF FFFF (SGR bit 14) 128MB Region 1


















