5-4 Vol. 3
PROTECTION
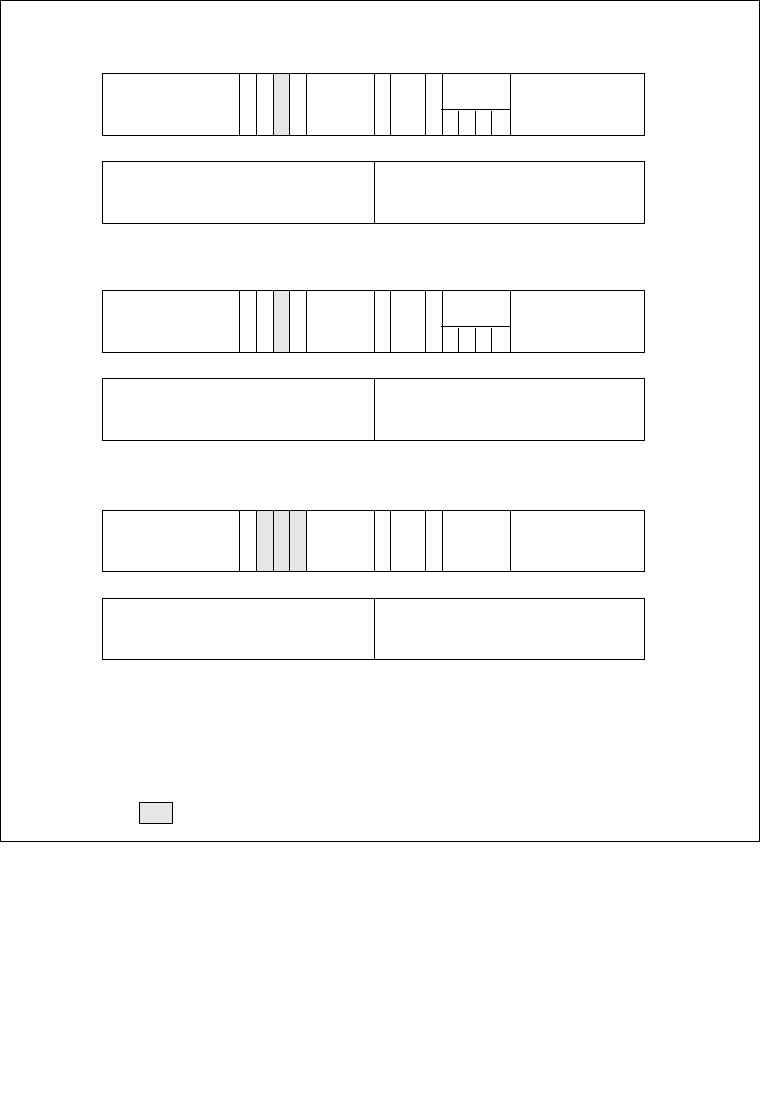
Many different styles of protection schemes can be implemented with these fields
and flags. When the operating system creates a descriptor, it places values in these
fields and flags in keeping with the particular protection style chosen for an operating
system or executive. Application program do not generally access or modify these
fields and flags.
Figure 5-1. Descriptor Fields Used for Protection
Base 23:16
31
2423 22
212019 16
15
13
14 12
11
87
0
P
Base 31:24
G
D
P
L
Type
1
0
4
31
16
15
0
Base Address 15:00
Segment Limit 15:00
0
Base 23:16
A
V
L
Limit
19:16
B
AWE0
Data-Segment Descriptor
31
24
23
22
212019 16
15
13
14 12 11
8
7
0
P
Base 31:24
G
D
P
L
Type
1
0
4
31
16
15
0
Base Address 15:00
Segment Limit 15:00
0
Base 23:16
A
V
L
Limit
19:16
D
ARC1
Code-Segment Descriptor
31
24
23
22
212019 16
15
13
14 12
11
8
7
0
P
Base 31:24
G
D
P
L
Type
0
4
31
16
15
0
Base Address 15:00
Segment Limit 15:00
0
Limit
19:16
System-Segment Descriptor
A
B
C
D
DPL
Accessed
Big
Conforming
Default
Descriptor Privilege Level
Reserved
E
G
R
LIMIT
W
P
Expansion Direction
Granularity
Readable
Segment Limit
Writable
Present
0
AVL Available to Sys. Programmer’s


















