Vol. 3 5-23
PROTECTION
The privilege checking rules are different depending on whether the control transfer
was initiated with a CALL or a JMP instruction, as shown in
Table 5-1.
The DPL field of the call-gate descriptor specifies the numerically highest privilege
level from which a calling procedure can access the call gate; that is, to access a call
gate, the CPL of a calling procedure must be equal to or less than the DPL of the call
gate. For example, in
Figure 5-15, call gate A has a DPL of 3. So calling procedures at
all CPLs (0 through 3) can access this call gate, which includes calling procedures in
code segments A, B, and C. Call gate B has a DPL of 2, so only calling procedures at
a CPL or 0, 1, or 2 can access call gate B, which includes calling procedures in code
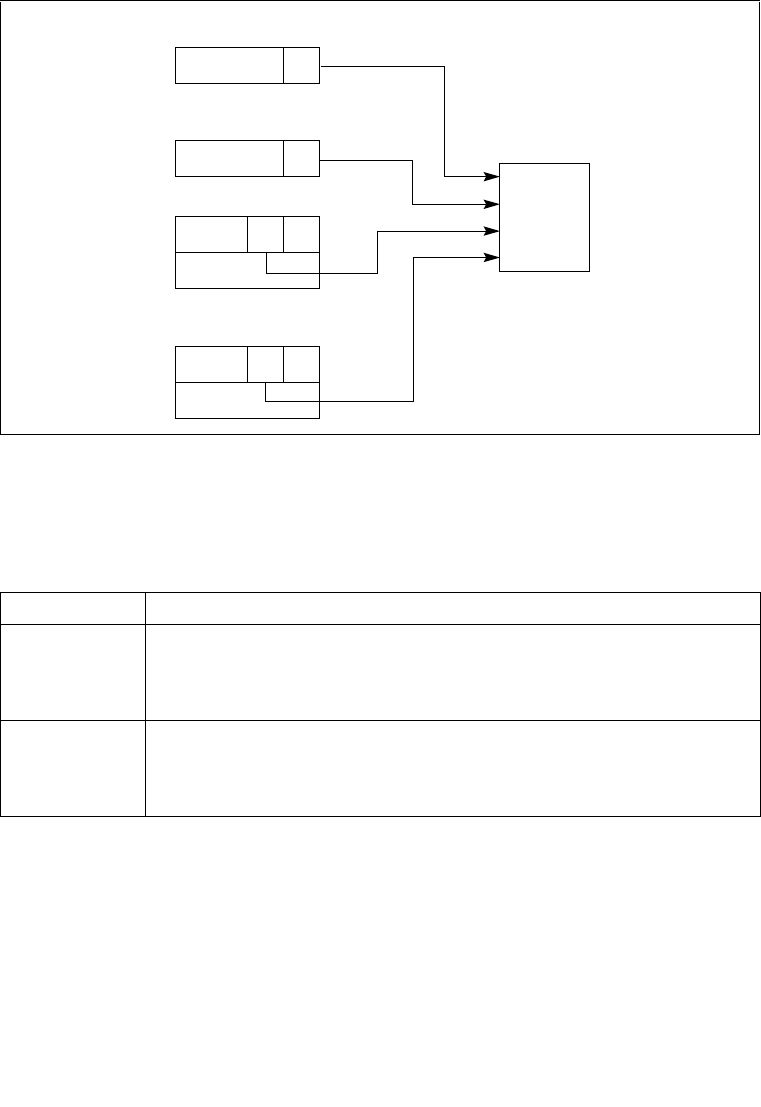
Figure 5-11. Privilege Check for Control Transfer with Call Gate
Table 5-1. Privilege Check Rules for Call Gates
Instruction Privilege Check Rules
CALL CPL ≤ call gate DPL; RPL ≤ call gate DPL
Destination conforming code segment DPL ≤ CPL
Destination nonconforming code segment DPL ≤ CPL
JMP CPL ≤ call gate DPL; RPL ≤ call gate DPL
Destination conforming code segment DPL ≤ CPL
Destination nonconforming code segment DPL = CPL
CPL
RPL
DPL
DPL
Privilege
Check
Call Gate (Descriptor)
Destination Code-
CS Register
Call-Gate Selector
Segment Descriptor


















