Hardware Reference Manual 93
Intel
®
IXP2800 Network Processor
Intel XScale
®
Core
There are several requirements for locking down code:
1. The routine used to lock lines down in the cache must be placed in non-cacheable memory,
which means the MMU is enabled. As a corollary: no fetches of cacheable code should occur
while locking instructions into the cache.
2. The code being locked into the cache must be cacheable.
3. The instruction cache must be enabled and invalidated prior to locking down lines.
Failure to follow these requirements will produce unpredictable results when accessing the
instruction cache.
System programmers should ensure that the code to lock instructions into the cache does not reside
closer than 128 bytes to a non-cacheable/cacheable page boundary. If the processor fetches ahead
into a cacheable page, then the first requirement noted above could be violated.
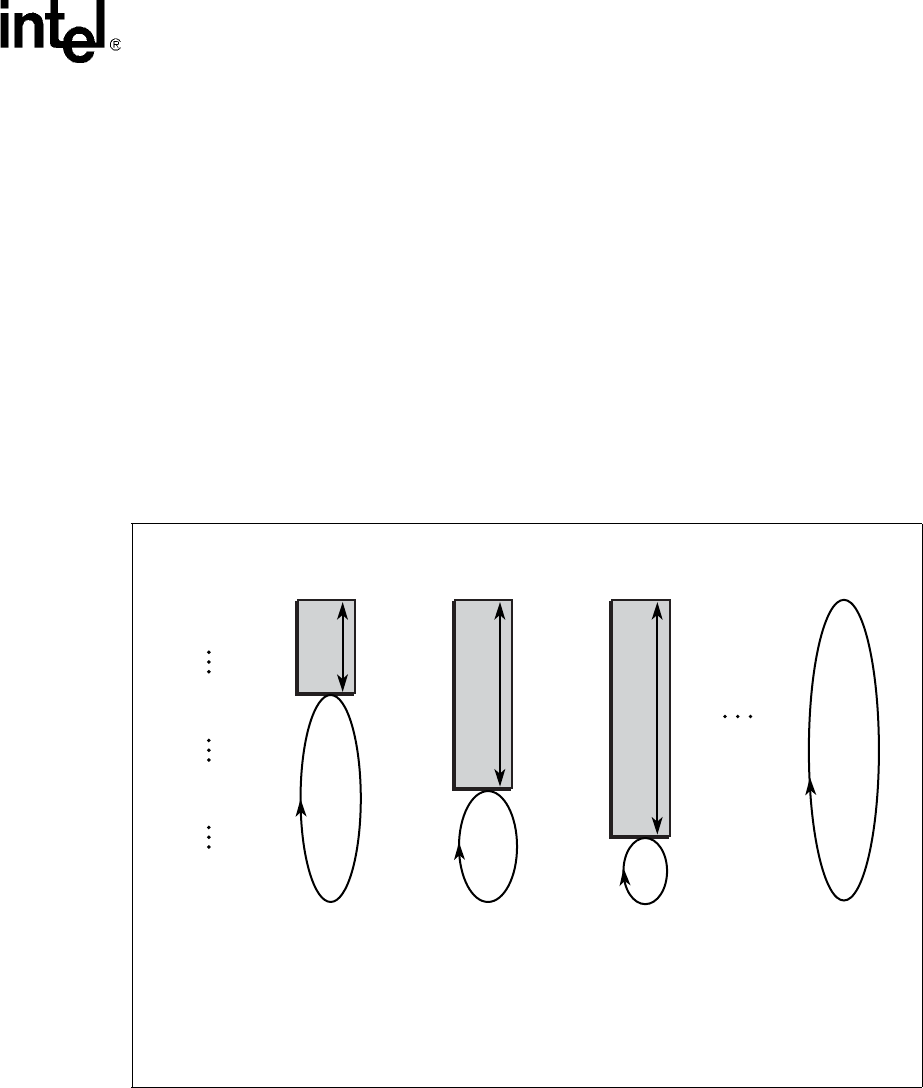
Lines are locked into a set starting at way 0 and may progress up to way 27; which set a line gets
locked into depends on the set index of the virtual address. Figure 19 is an example of where lines
of code may be locked into the cache along with how the round-robin pointer is affected.
Software can lock down several different routines located at different memory locations. This may
cause some sets to have more locked lines than others as shown in Figure 19.
Figure 19. Locked Line Effect on Round Robin Replacement
A9686-01
Locked
Notes:
set 0: 8 ways locked, 24 ways available for round robin replacement
set 1: 23 ways locked, 9 ways available for round robin replacement
set 2: 28 ways locked, only way 28-31 available for replacement
set 31: all 32 ways available for round robin replacement
way 0
way 1
way 7
way 8
way 22
way 23
way 30
way 31
set 0
Locked
set 1
Locked
set 2 set 31


















