381 | WirelessIntrusionPrevention DellPowerConnectW-SeriesArubaOS6.2 | User Guide
Configuring Intrusion Protection
Intrusion protection features support containment of an AP or a client. In the case of an AP, we will attempt to
disconnect all client that are connected or attempting to connect to the AP. In the case of a client, the client's
association to an AP is targeted. The following containment mechanisms are supported:
l Deauthentication containment: An AP or client is contained by disrupting its association on the wireless
interface.
l Tarpit containment: An AP is contained by luring clients that are attempting to associate with it to a tarpit. The
tarpit can be on the same channel as the AP being contained, or on a different channel (see "Working with Tarpit
Shielding" on page 392).
l Wired containment: An AP or client is contained by disrupting its connection on the wired interface.
The WIP feature supports separate enforcement policies that use the underlying containment mechanisms to
contain an AP or a client that do not conform to the policy. These policies are discussed in the sections that follow.
Understanding Infrastructure Intrusion Protection
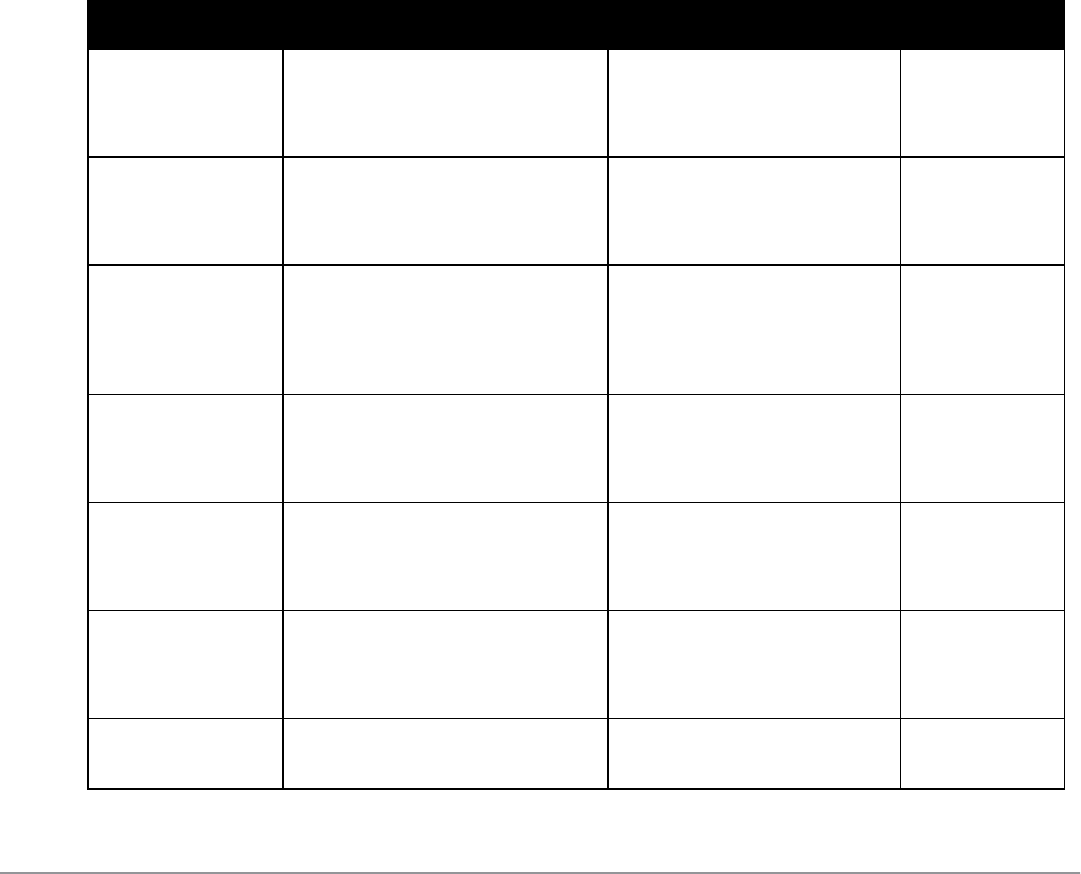
Table 107 presents a summary of the infrastructure intrusion protection features with their related commands, traps,
and syslog identifications. Details of each feature follow the table.
Feature Command Trap Syslog ID
"Protecting 40MHz
802.11 High
Throughput Devices"
on page 382
ids unauthorized-device-profile
protect-ht-40mhz
wlsxAPDeauthContainment
wlsxClientDeauthContainment
wlsxTarpitContainment
106005, 106006,
126102, 126103,
126108, 127102,
127103, 127108
"Protecting 802.11n
High Throughput
Devices" on page 382
ids unauthorized-device-profile
protect-high-throughput
wlsxAPDeauthContainment
wlsxClientDeauthContainment
wlsxTarpitContainment
106005, 106006,
126102, 126103,
126108, 127102,
127103, 127108
"Protecting Against
Adhoc Networks" on
page 382
ids unauthorized-device-profile
protect-adhoc-network
wlsxAPDeauthContainment
wlsxClientDeauthContainment
wlsxTarpitContainment
106005, 106006,
126012, 126102,
126103, 126108,
127102, 127103,
127108
"Protecting Against
AP Impersonation " on
page 382
ids impersonation-profile
protect-ap-impersonation
wlsxAPDeauthContainment
wlsxClientDeauthContainment
wlsxTarpitContainment
106005, 106006,
126102, 126103,
126108, 127102,
127103, 127108
"Protecting Against
Misconfigured APs"
on page 382
ids unauthorized-device-profile
protect-misconfigured-ap
wlsxAPDeauthContainment
wlsxClientDeauthContainment
wlsxTarpitContainment
106005, 106006,
126102, 126103,
126108, 127102,
127103, 127108
"Protecting SSIDs" on
page 382
ids unauthorized-device-profile
protect-ssid
wlsxAPDeauthContainment
wlsxClientDeauthContainment
wlsxTarpitContainment
106005, 106006,
126102, 126103,
126108, 127102,
127103, 127108
"Protecting Against
Rogue Containment"
ids unauthorized-device-profile
rogue-containment
wlsxAPDeauthContainment
wlsxClientDeauthContainment
106005, 106006,
126102, 126103,
Table 107:
Infrastructure Protection Summary


















