843 | DellPowerConnectW-SeriesArubaOS6.2 | User Guide
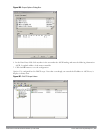
Figure 408: IAS RADIUS Clients
3. To configure a RADIUS client, select Action > New RADIUS Client from the menu at the top of the window.
4. In the New RADIUS Client dialog window, enter the name and IP address for the controller. Click Next.
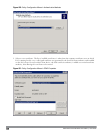
5. In the next window that appears, enter and confirm a shared secret. The shared secret is configured on both the
RADIUS server and client, and ensures that an unauthorized client cannot perform authentication against the
server.
6. Click Finish.
Remote Access Policies
The IAS policy configuration defines all policies related to wireless access, including time of day restrictions, session
length, authentication type, and group-related policies. See Microsoft product documentation for detailed
descriptions and explanations of IAS policy settings.
Active Directory Database
The Active Directory database serves as the master authentication database for both the wired and wireless
networks. The IAS authentication server bases all authentication decisions on information in the Active Directory
database. IAS is normally used as an authentication server for remote access and thus looks to the Active Directory
“Remote Access” property to determine whether authentication requests should be allowed or denied. This property
is set on a per-user or per-computer basis. For a user or computer to be allowed access to the wireless network, the
remote access property must be set to “Allow access”.
The authentication policy configured in IAS depends on the group membership of the computer or user in Active
Directory. These policies are responsible for passing group information back to the controller for use in assigning
computers or users to the correct role, which determines their network access privileges. When the IAS server
receives a request for authentication, it compares the request with the list of remote access policies. The first policy
to match the request is executed; additional policies are not searched.
Configuring Policies
The policies in this 802.1x authentication example are designed to work by examining the username portion of the
authentication request, searching the Active Directory database for a matching name, and then examining the group