990
Chapter 53 Fixed Mode-Reset Vector / BOOT-ROM
5.Bootloader Update Strategy
5. Bootloader Update Strategy
Some applications require the possibility of software updates in the final product without great effort. To be able to
program an updated application to the microcontroller, all connected busses (I2C, CAN, LIN, K-Line etc.) can be
used, so that the microcontroller can remain ‘embedded’ in a bigger system.
But therefore a user bootloader has to be integrated to the application software, which handles the startup of the
application, the requests for new programming and the application update itself.
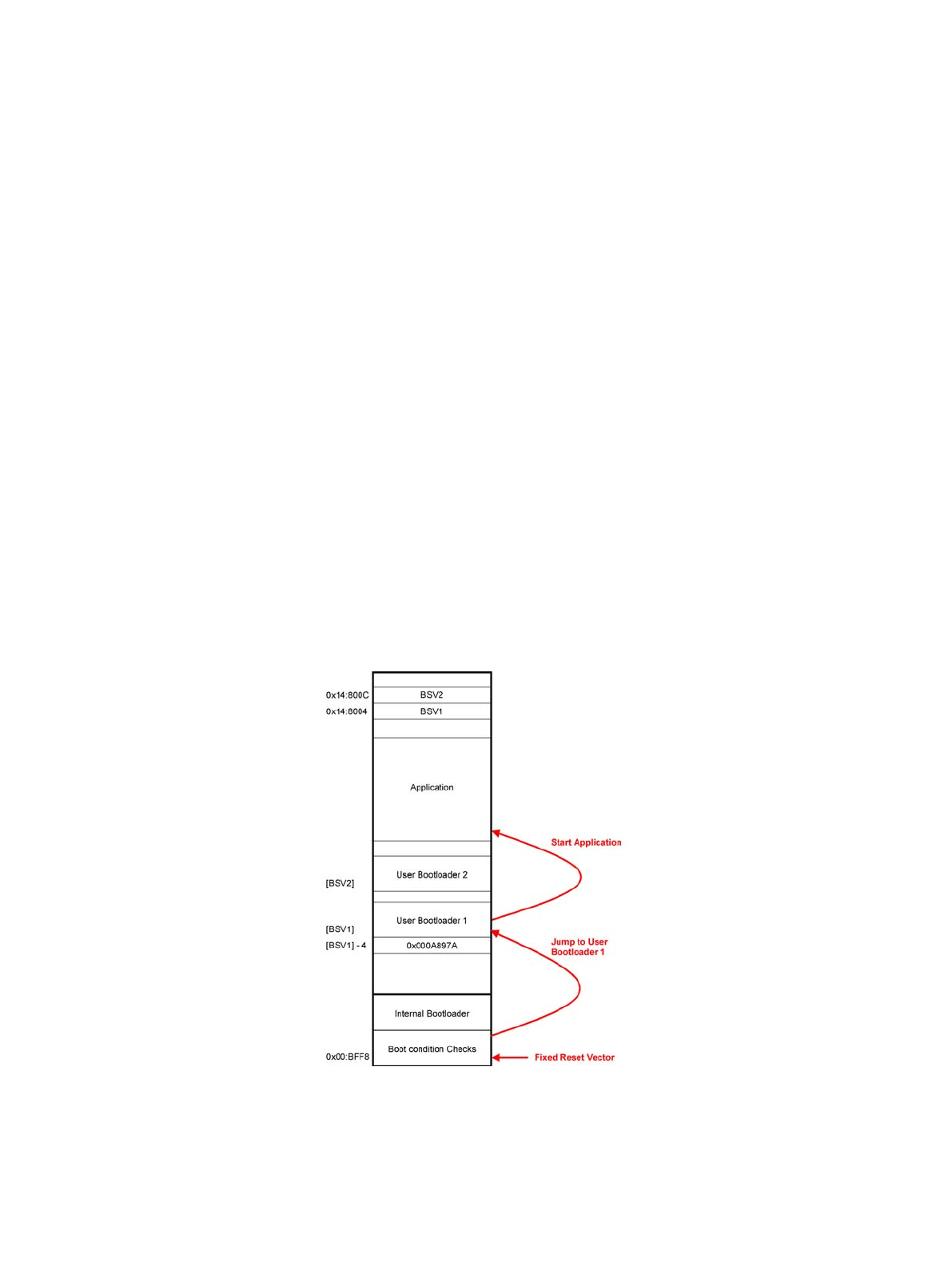
This user bootloader should be executed after every reset command, so the Boot Security Vector should point to
the starting address of this bootloader. The request for re-programming the application has to be done by a defined
communication protocol.
If the Boot Security Vector feature is used, there is also no possibility to enter the internal bootloader of the
microcontroller. So the code is secured from read-out or manipulation.
If there is a request for updating an application, the user bootloader causes the erase of flash sectors where the
application is located. Flash section, where the Boot Security Vector is located and the section of the bootloader
itself may not be erased. After erasing, the bootloader has to handle the programming of the application.
If during this procedure problems like reset or power-down occur, the program-ming can be started again without
problems because user bootloader and Boot Security Vector are not changed.
This system brings along some problems if the user bootloader has to be updated. Therefore also the user
bootloader sector has to be erased and re-programmed. If there is a reset or power-down before ending the
programming, there is no valid bootloader anymore and there will be no access to the microcontroller via the above
mentioned busses.
All MB91460 series flash devices therefore offer the possibility of a safe bootloader update by use of two Boot
Security Vectors and a Magic Number.
If user bootloader 1 is valid, set the Magic Number, which has to be located on the four bytes before the address
defined by BSV1, to 0x000A897A. So after every reset this bootloader is executed. If there is no request for a re-
programming, the application is started normally.